Le Tour Du Hack 2021
"Life is not a problem to be solved, but a reality to be experienced." Soren Kierkegaard

Welcome! I'm glad you're here. We need more people like you.
This blog will be about the LTDH21 annual flagship event organised by ENUSEC - a student society interested in all aspects of security based in Edinburgh. This is not a walkthrough although I plan to cover a few challenges that we solved in a future blog post.
If you're planning to make a living in defense, you have to think like the offense.
Participate and learn to win in Capture the Flag (CTF). These types of competitions are based on disciplines of professional computer security into short objective and quantifiable exercises. The main focus area for CTF competitions is to measure the vulnerability discovery, exploit development, toolkit creating, and operational tradecraft.
Whether you want to succeed at CTFs or in a computer security professional job, you'll need to become an expert in at least one of these disciplines. Ideally as many as possible.

A little bit about CTFs if you've never participated in one before. CTFs are events that are usually hosted at information security conferences, These events consist of a series of challenges that vary in their degree of difficulty, and that require participants to exercise different skillsets to solve. Once an individual challenge is solved, a "flag" is given to the player and they submit this flag to the CTF server to earn points. Players can be lone wolves who attempt the various challenges by themselves, or they can work with others to attempt to score the highest number of points as a team.
CTF events are usually timed, and the points are totalled once the time has expired. The winning player / team will be the one that solved the most challenges and thus secured the highest score.
Types of Events - The two most common types are:
Red Team/Blue Team - In this style of event the red team attempts to capture flags while the blue team attempts to defend the various flags from being captured.
Red Team - Usually involves one or more people, working alone or on a team, who attempt to capture various flags while there is no team defending them.
Types of Challenges - Some popular areas of focus are:
Programming - Usually require some sort of programming to solve. In most cases, it will involve a mixture of programming and some reverse engineering.
Crypto - feature common "real world" algorithms or scenarios that often include the ever-popular ransomware type of malware.
Web - Usually vulnerabilities that are in OWASP top 10.
Reverse Engineering - Typically the process of taking a compiled machine code - bytecode program and converting it back to a more human readable format.
OSINT - Known as Open-source intelligence, you will be required to dig deep to find old information like a user's first tweet for example.
Pwn - In this challenges you usually have to buffer overflows, by using the ctf framework called pwntools you will dev your python exploit.
Misc - miscellaneous challenges these are a bit random, can be various types.
Okay, let's talk about the event.
I was notified about this virtual event taking place by a fellow member of the Ethical Hacking Society at GCU, I never participated before in any of ENUSEC's CTFs, I know their first Le Tour Du Hack took place in 2017. I simply couldn't let the opportunity pass, as usual I am very busy, involved in a few projects but I thought; what's the worst that could happen? I must try this CTF.
So I signed up, the event was running for a 2 day CTF for all abilities! Top 3 teams to win the following Prizes:
1st Place -> £1000
2nd Place -> £500
3rd Place -> £250
And they also had 50 free LTDH21 swag bags to a lucky 50 participants, including a T-shirt and other goodies, Thanks to SecureWorks for sponsoring this wonderful event.
The event started on Sat, 19 Jun 2021 at 10:00 am and it was finishing on Sun, 20 Jun 2021, 19:00 BST. To begin with we were a team of two for most of Saturday and then in the evening I seen another mate was competing alone so I invited him to join us.
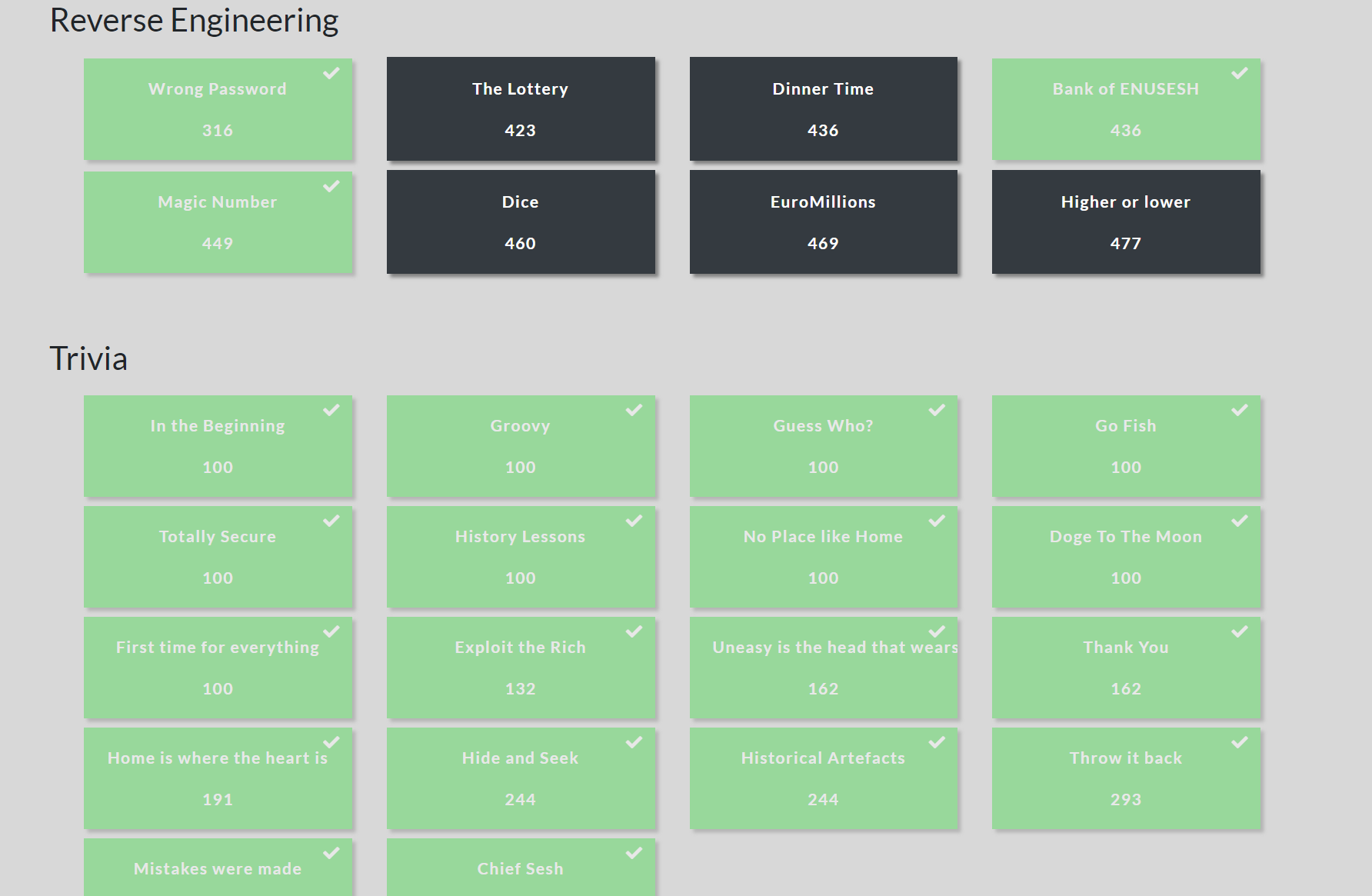
Within two hours we already had over 4k points and grinding away to climb the leaderboard, we were on 8th and rocking. We had managed to complete 30 challenges from the misc, reverse engineering, osint (trivia), and web categories. I was chuffed with the result so far because I wasn't thinking we would do so well. My personal aim was to be in Top10 at least and just enjoy the event.
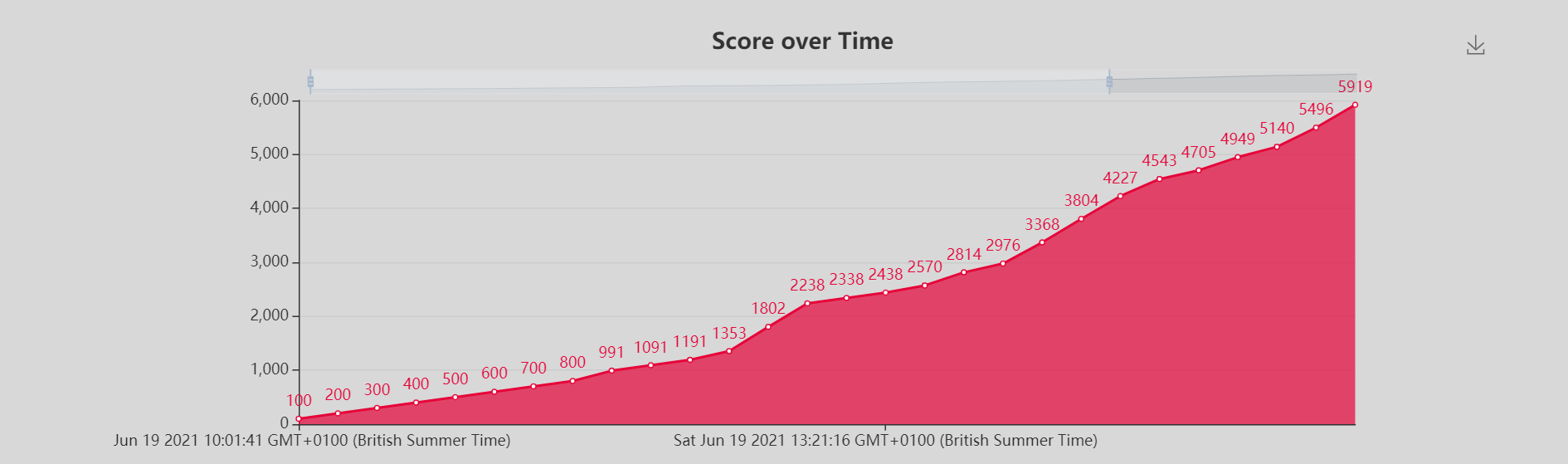
Finished the saturday around 23.00 and started again on Sunday we were mainly going over the challenges we couldn't solve the previous day. I convinced a few other mates to join and we were now a team of five. It was a slow day because we had only the hardest of challenges to solve, we then started dropping a few places on the leaderboard however I was still happy that we remained in Top 10 till nearly towards the end of the event, we were not chasing to win this event but to have fun, we had a tiny team put together very fast at last second unlike other teams who had 10 to 15 members. 👀
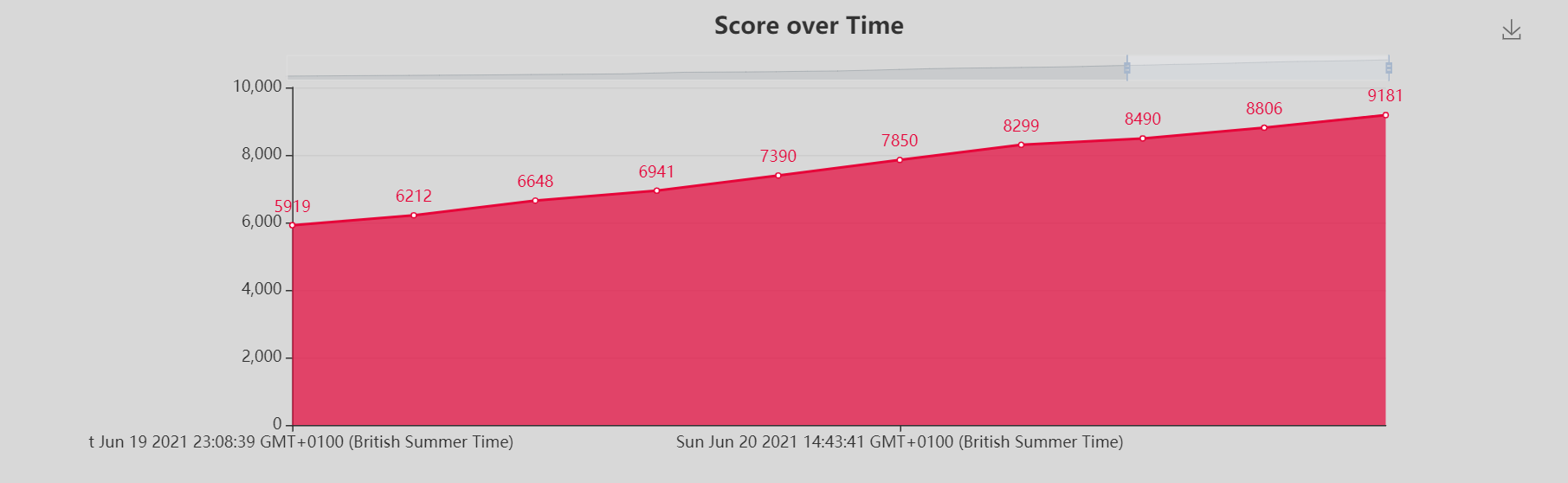
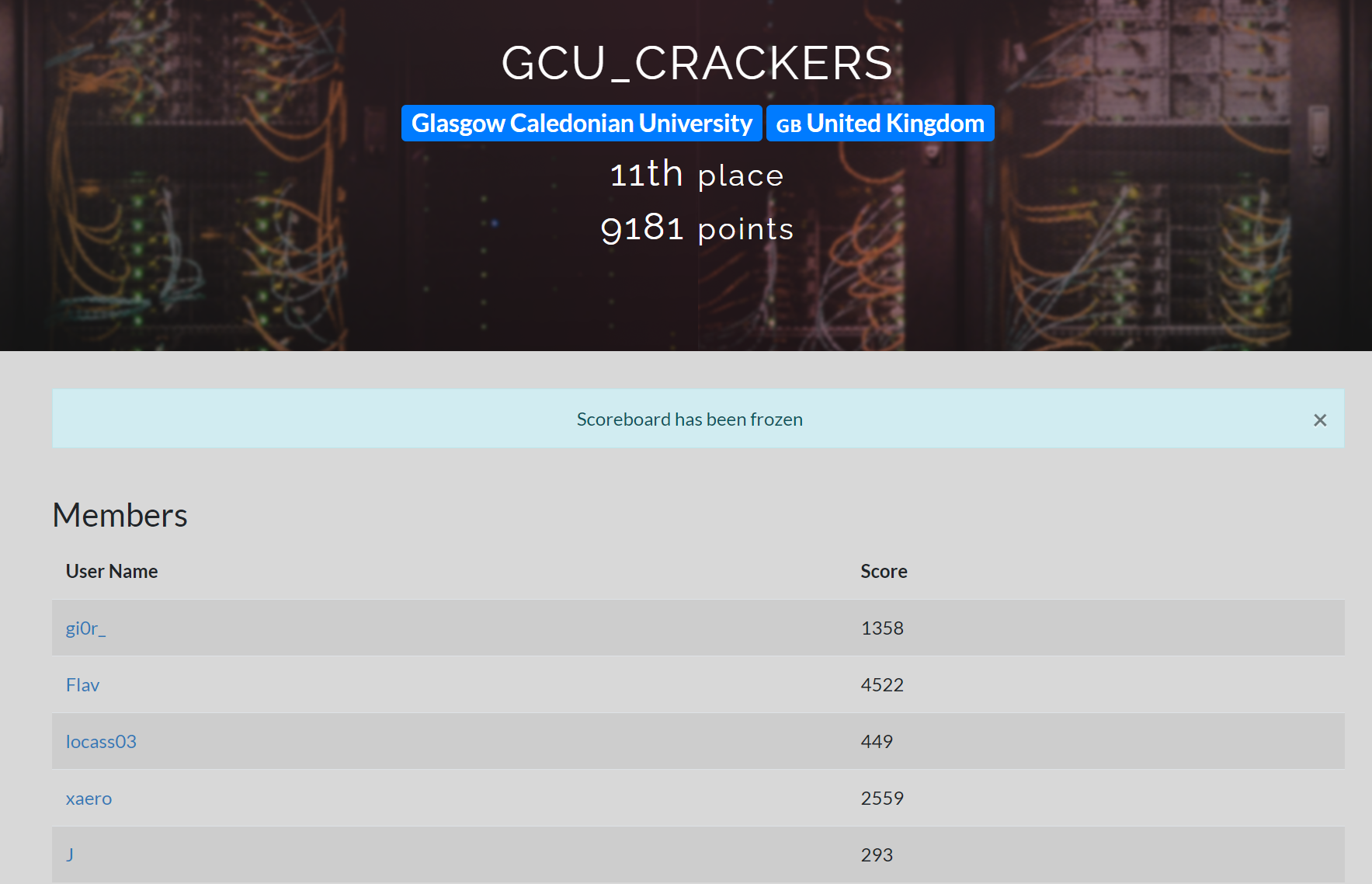
We managed to solve another 7 challenges and settled on 11th place. We were really close to a few Web challenges but couldn't quite figure out the last part to get the flags.
I have to say I totally enjoyed this CTF and I will definitely recommend it to beginners, I would say the challenges were not too hard, unlike other events I have been such as Hack The Box University CTF, Try Hack Me (HackBack) or pwnED.
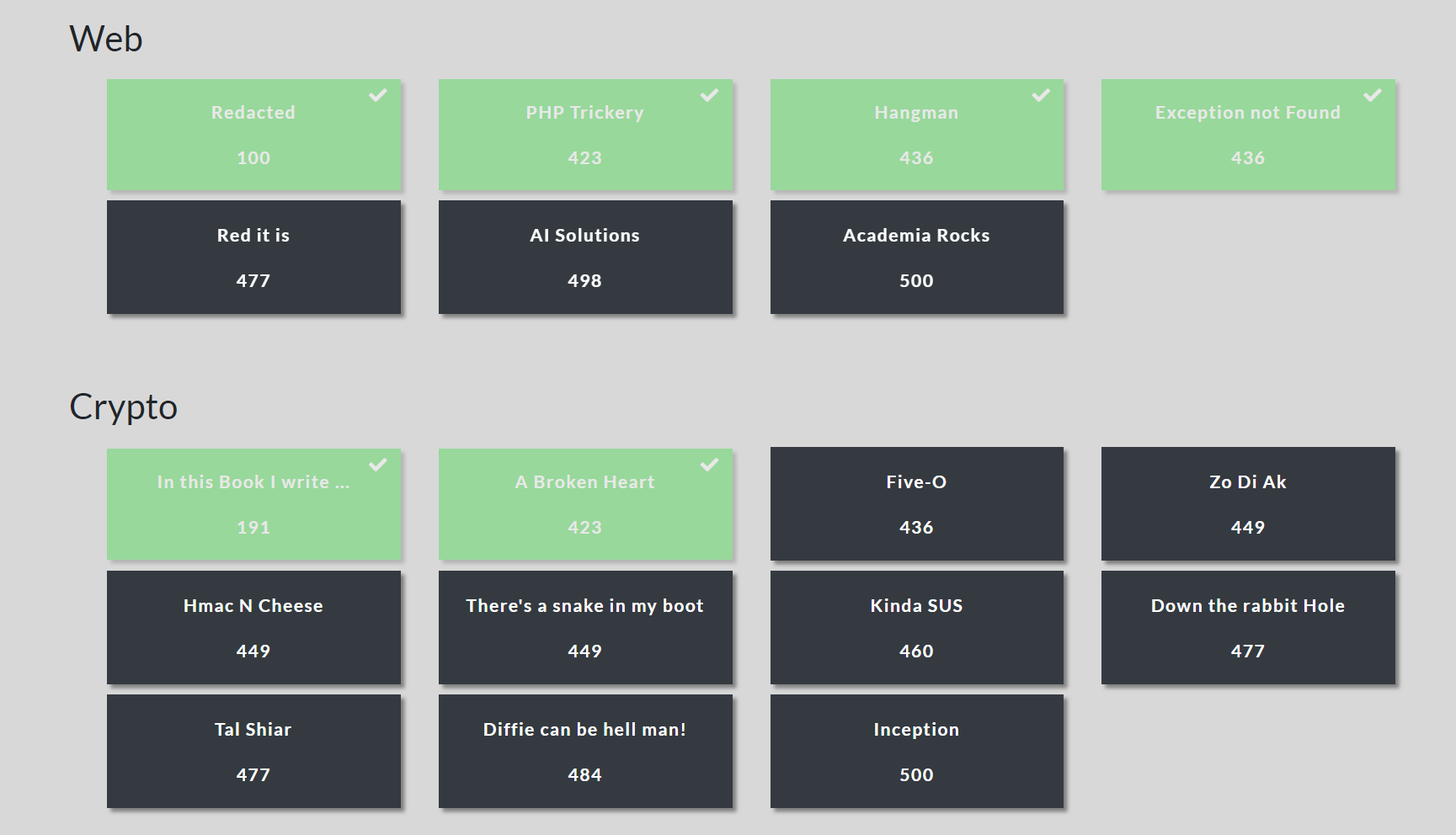
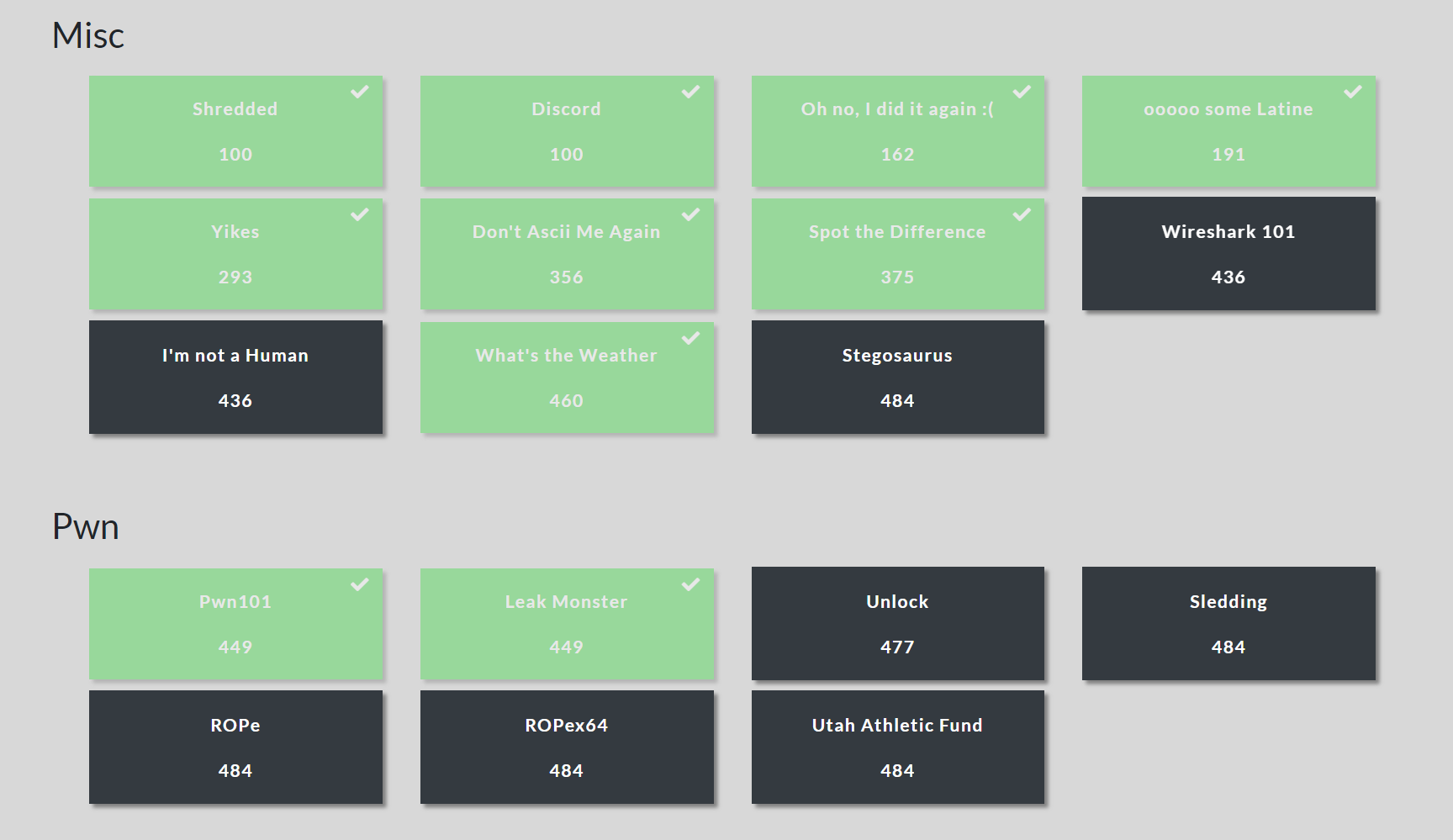
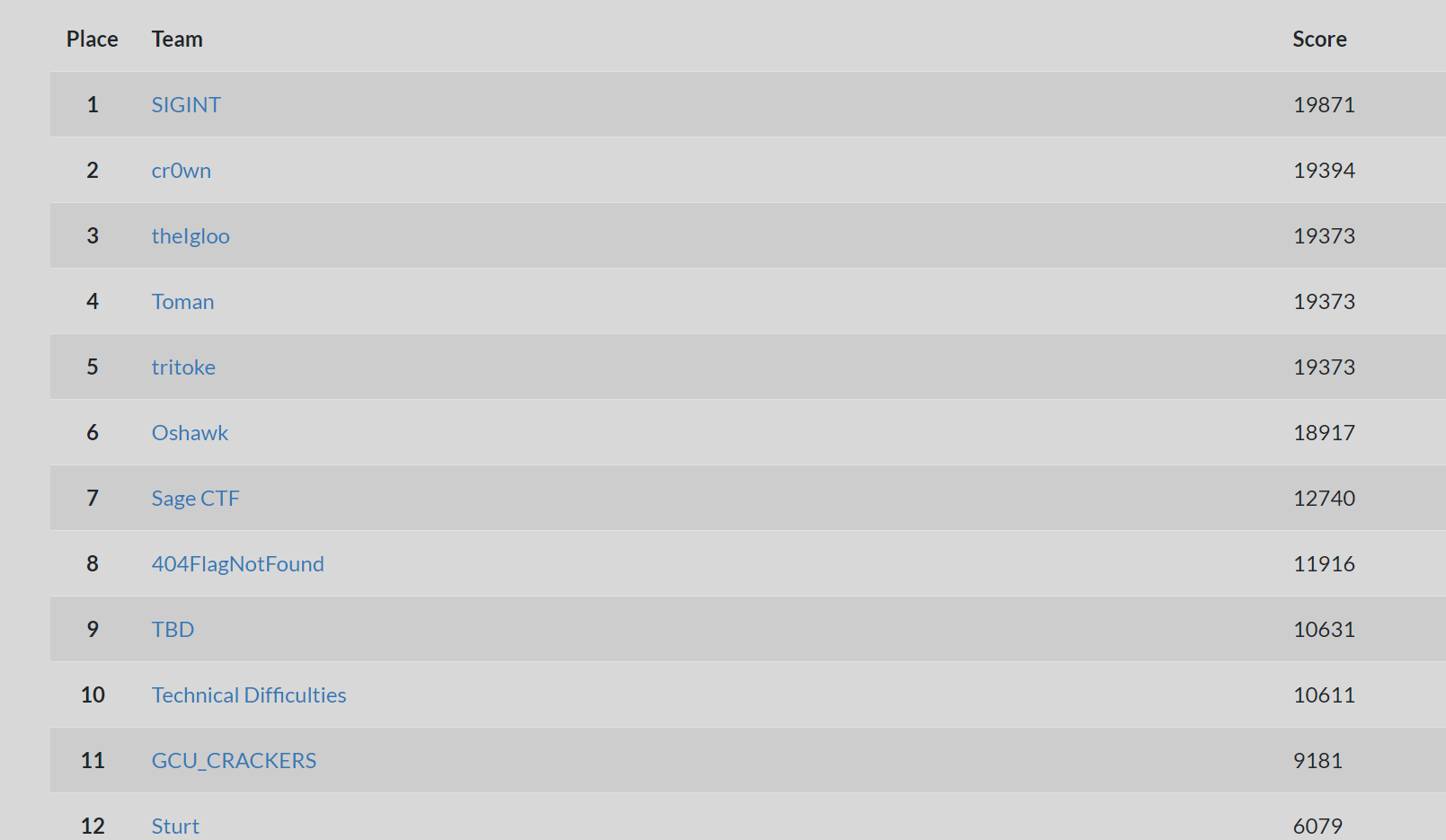
Congrats to SIGINT, crOwn and theIgloo (Abertey Hackers) for winning the competition!
And many thanks for my fellow team mates for their participation in the CTF, couldn't do it without you. We have learned a ton and had a great weekend, If time allows; I will post a follow up blog of how we solved a few of the challenges.
I hope face to face CTFs will be allowed again soon. I'm getting flashbacks of 🡣 our last in person CTF.

To be continued ...
Have you got any suggestions for me ? Get in touch!
Thank you for reading my article, Until next time!
Your friendly neighbourhood Hacker.
