What does it take to be a web application security consultant?
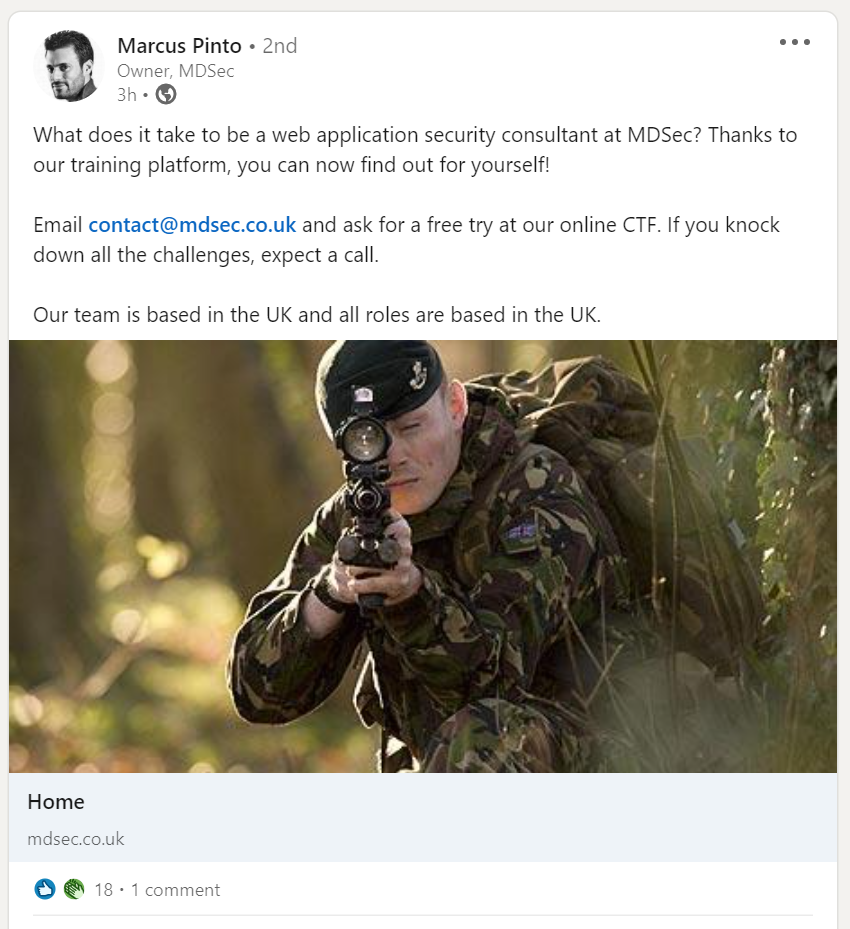
Very recently, I participated in a CTF. While I was still in the zone, I came across an interesting post on LinkedIn that said What does it take to be a web application security consultant?
The author was Marcus Pinto, Owner of MDSec, a security consulting and education company with expertise that is backed by the Web and Mobile Application Hackers Handbook series.
The post stated that if you want to see what it takes to be a web application security consultant, check out the free training platform. To join, the applicant would send an e-mail to [email protected] and request an account on the free CTF portal. They stated that if you knock down all the challenges expect a call (perfect for job seekers!).
This got me intrigued. What does a CTF set up by a top security company look like?
Sent an e-mail and asked for access, got an e-mail back very promptly with the account details and a few instructions.
Content:
The content here will give you insight into:
- Uncovering subtle flaws in applications
- Expanding your armory of tools and techniques
- Writing custom code (burp extensions
- Practicing key vulnerabilities
Prerequisite Knowledge:
It is assumed that you have a working knowledge of:
- Burp Proxy, Intruder, Repeater, Scanner
- At least one programming language (python etc.)
- HTML
- Basic understanding of SSL
- HTTP
- JavaScript
- The OWASP Top 10
- XSS, SQLi, Traversal
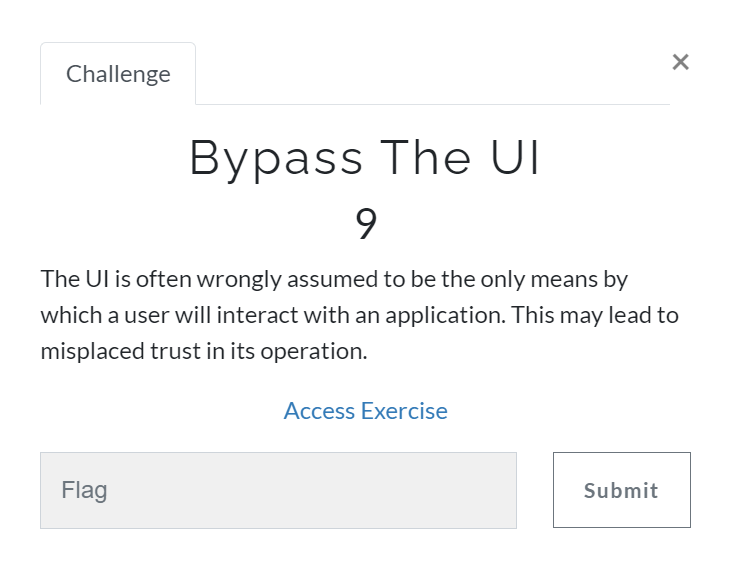
The starting point is the challenges in the interview section. The difficulty ranges from low to hard. There is no requirement to connect to a private network, although Burp or Owasp ZAP will be needed later. Each challenge has an introductory description and sometimes even a hint to help you get started.
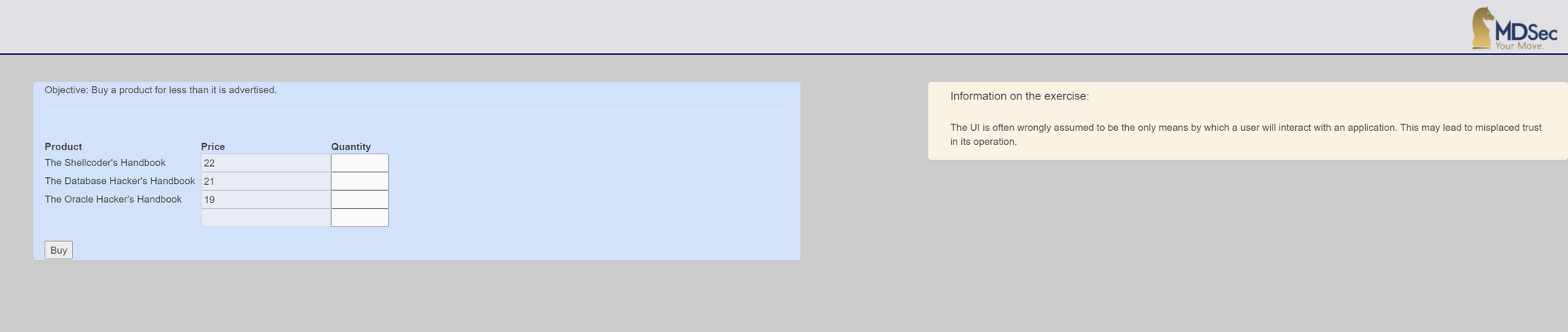
My aim is to share this great opportunity with those looking for a job within the UK. It is also great for those who like a challenge and hands-on practice.
MDSec also offers the following training:
- Adversary Simulation and Red Team Tactics
- Beyond the Web Application Hackers Handbook (Advanced)
- The Mobile Application Hackers Handbook, Live Edition
- The Web Application Hackers Handbook, Live Edition (Beginner Course)
I am not affiliated or being paid to advertise the above courses. If you like or could not solve the challenges, you can sign up for the (Advanced) course (in this case). This will teach you the methodology you need to solve them.
Conclusions
So what does it take to be a web application security consultant?
For some companies it takes a Cyber Security degree, and for some it could be as little as solving web app challenges as proof of your skill.
Application security is fast becoming the most challenging aspect of information technology. Not surprisingly, it drives demand for highly skilled consultants.
Top Required Skills for a Security Consultant
Students planning to become security consultants should learn hard skills such as computer programming, network, and security configuration. Taking courses like cloud computing infrastructure and services, network and security foundations, will prepare you to understand the complicated technical aspects of security consulting.
Though it's natural to gravitate towards certain soft skills over others, students can highly strengthen areas such as communication, problem-solving, and leadership skills by obtaining a degree. Courses in critical thinking and logic, communication, and managing IT can prepare you for leadership in the field.
Security consultants need to engage in critical thinking to analyse security issues and respond quickly to breaches—or even better, find problems before they arise. Communication is also very essential, as they must communicate with top executives about the company's security operations, outlining issues so that managers can both understand and make informed decisions. Security consultants may need to communicate via written reports or through oral presentations, and they may also be called upon to tutor non-IT staff in best practices.
Security consultants who develop leadership skills and strong management techniques can advance to oversee entire departments and projects. Many companies employ teams of IT personnel, which good managers can lead to implement and maintain their cybersecurity protocols.
About MDSec's Web Challenges
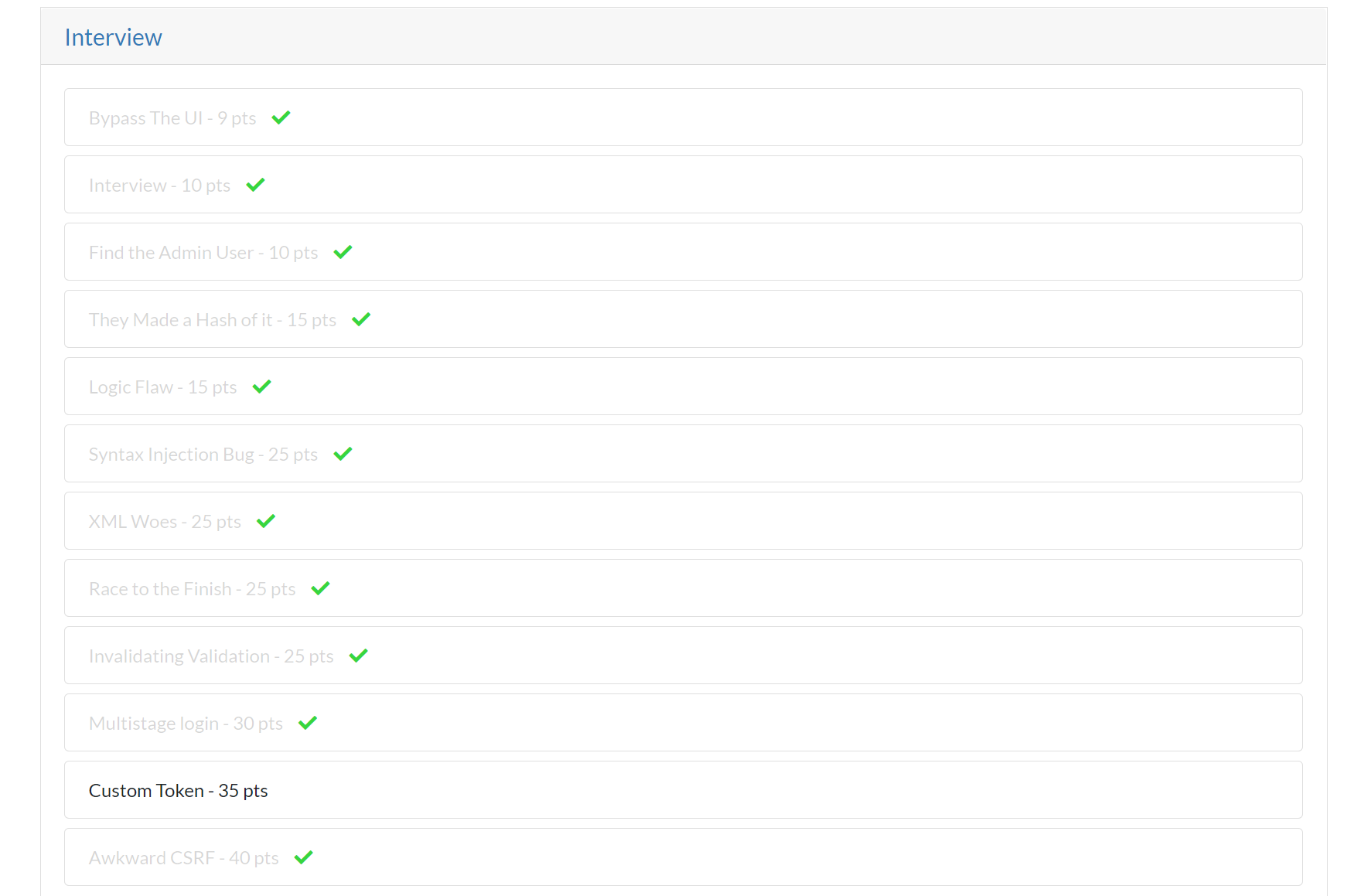
I thoroughly enjoyed the challenges so far. You can see I still have one challenge left to complete from the Interview section.
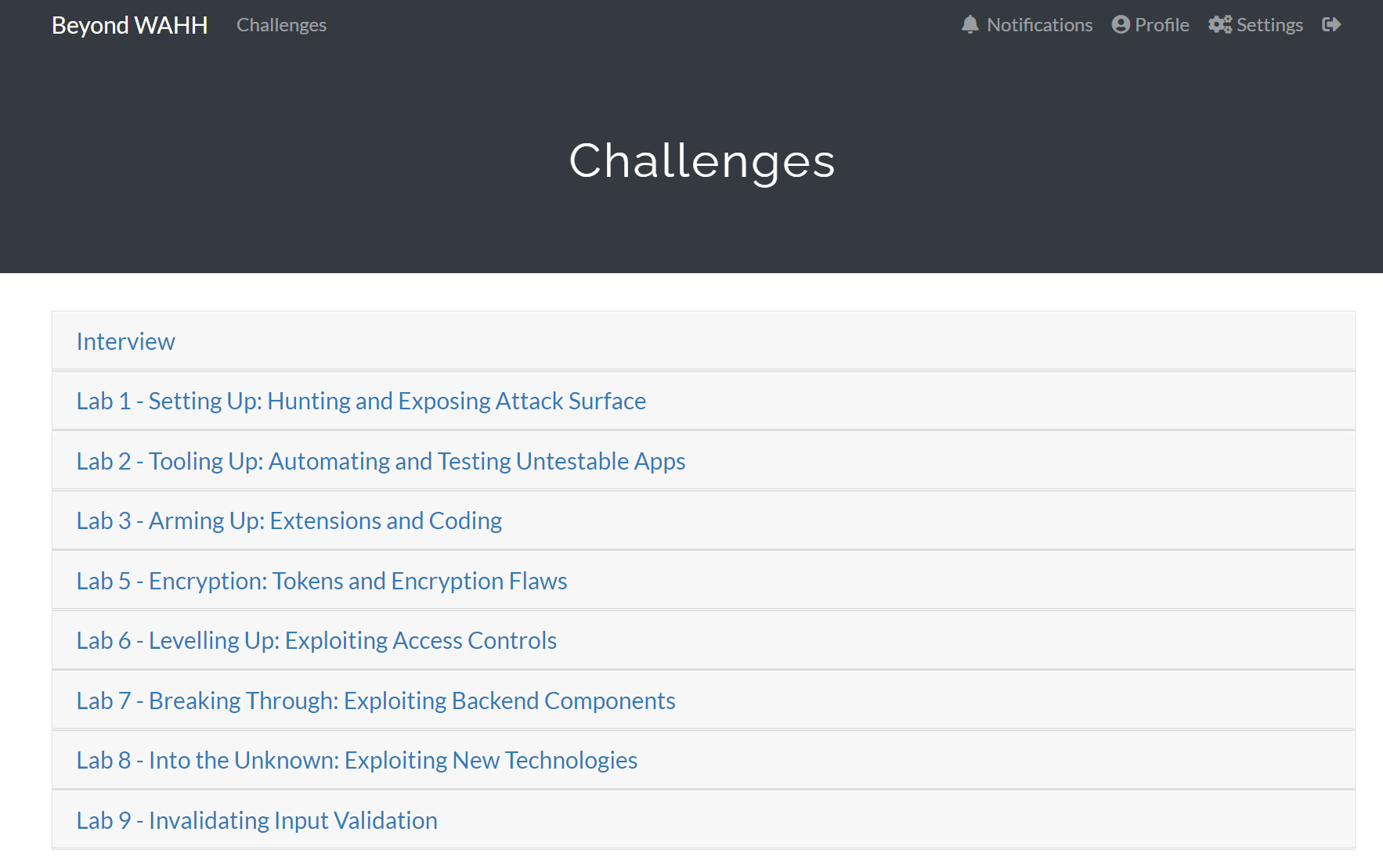
You can probably imagine a few of the challenges take time to figure out. Especially the challenges that you have not encountered before. There are nine more labs to which I do not have access yet, but I assume each lab will be unlocked after I complete the Interview section.
The exercises were very realistic to what kind of vulnerabilities are hiding in modern web applications. I like Web testing, but there is so much to it. The best approach, in my opinion, is practicing; you will get a lot of exposure and gain knowledge with a hands-on approach from different sources.
There are a lot of platforms paid and free to practice and, by sticking to just one or two, in my opinion, you limit yourself. Explore and find different avenues every time an opportunity is presented.
PS: Don't ask Marcus for hints! You won't get any. 😇
Have you got any suggestions or questions for me ? Get in touch!
Thank you for reading my article, Until next time!
Your friendly neighbourhood Hacker.
