Glad I could help the NHS with this issue..
Introduction
So yeah you might have guessed, like my previous post, this is another subdomain takeover, I'm telling you.. this has became addictive.
Before we move on please see /disclaimer/
So let's start, doing my usual enumeration with subfinder on *.nhs.uk I found many... many... possible vulnerable domains to hijack. I noticed that a lot of NHS's infrastructure is running from Microsoft Azure's servers.. I already know that domains using these services can be easily taken over if they aren't registered.
*.trafficmanager.net
*.azurewebsites.net
*.azureapp.com
*.azureedge.net
On my prior post the vulnerable domain was on a *.azureedge.net, this time the subdomain that caught my attention was on *.azurewebsites.net and returning 404 error.
Performing a dig on the subdomain returned the CNAME and that's all I needed for my next step to check if this can be taken over. I was pretty confident this will work so I went ahead and logged into my Azure portal and started to create a Web App using the vulnerable subdomain name.
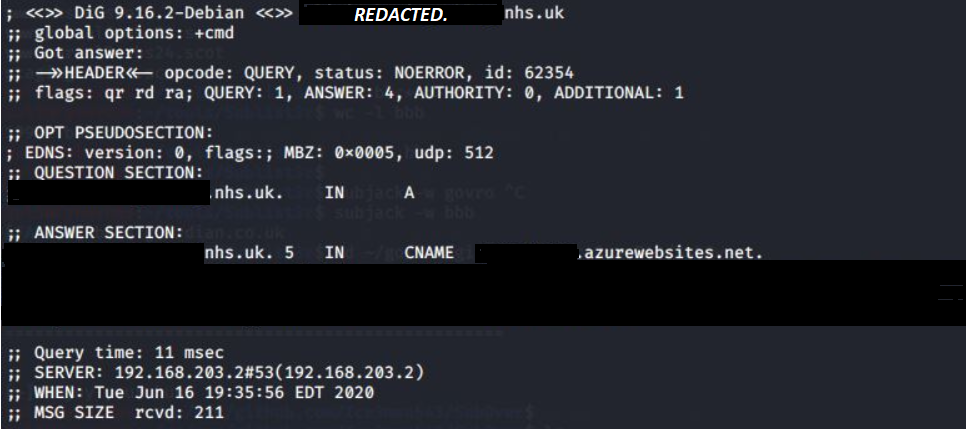
Exploiting / PoC
Pretty excited when I seen the green tick, I then proceeded to create a small PoC html file and uploaded it through FTP on the server. Visiting the main domain url confirmed the take over was successful. I even installed SSL on the domain! :)
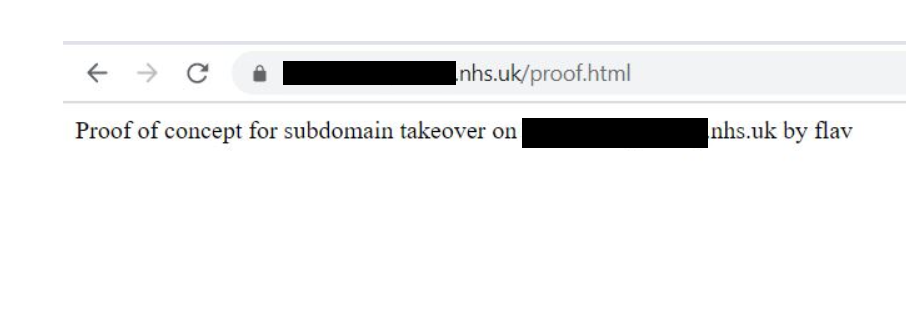
Reporting
I wrote all my steps in a simple format to be replicated by the NHS digital team if in doubt, here is the the introduction e-mail I sent them.
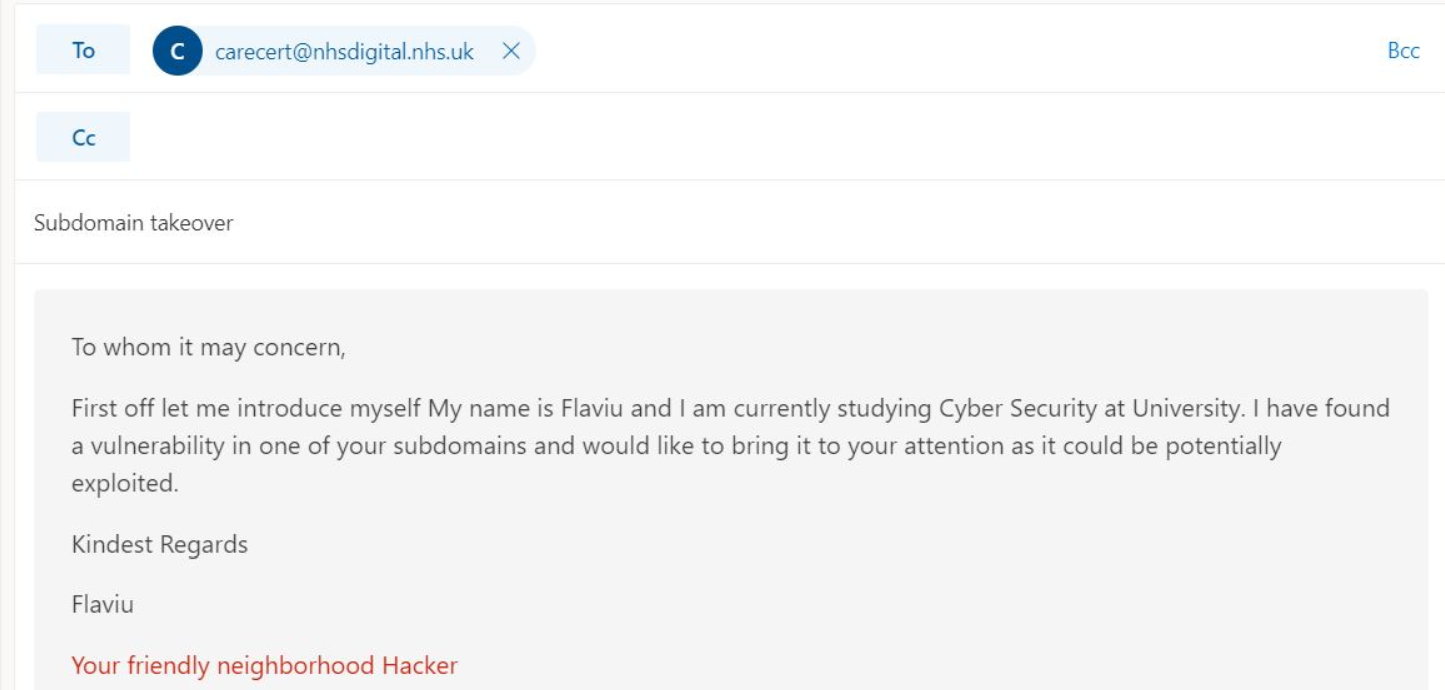
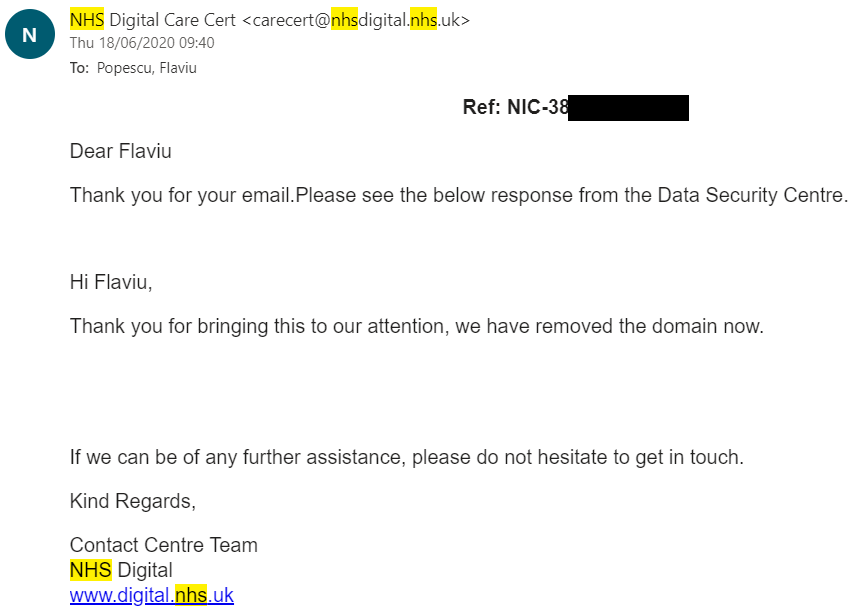
A few moments later....
In my reports I always make suggestions to mitigate the issue that I'm reporting, here were my suggestions to the NHS team.
- Remove the DNS record from the DNS zone if it is no longer needed.
- Claim the domain name in a permanent DNS record so it cannot be used elsewhere.
Pretty straight forward and simple instructions, I can confirm they have now disabled that subdomain in question and I'm glad they did.
Impact
A malicious user could create any web page with any content and host it on the vulnerable domain. This would allow them to post malicious content which would be mistaken for a valid website. They could steal cookies, bypass domain security, steal sensitive user data, malware distribution, etc.
In my next post I will talk about other cloud providers that are vulnerable to this types of attacks.
Thank you for reading my article, Until next time!
Read more about Other Vulnerable Cloud Providers
Your friendly neighbourhood Hacker.
