How I took over a subdomain from the U.S Army Headquarters
Introduction
I have recently signed up to HackerOne and went through all the checks required in order to have a qualifying account for Bug Bounty, below are the steps required by HackerOne.
- Bookmark 5 programs on the Directory
- Upvote 5 items on Hacktivity
- Earn at least 26 points on the Hacker101 Capture the Flag
- Submit your first valid report. Learn more about submitting reports.
Before we move on please see /disclaimer/
While I was performing my usual Recon and Subdomain Enumeration I came across numerous subdomains for D.o.D that had CNAMES resolving to Azure CDN Profiles.
A brief explanation on CNAME (Canonical Name Record) subdomain takeover method:
A domain name is using a CNAME record to another domain
(e.g. subdomain.company.com CNAME anothercompany.com).
At some point, anothercompany.com expired and will be available for registration by anyone.
Since the CNAME record is not been updated from company.com DNS zone, anyone who registers anothercompany.com has full control over subdomain.company.com until the DNS record is set.
Enumeration
For my enumeration I use a kali VM where I have subfinder from projectdiscovery, with this fantastic tool I am able to find subdomains.
After half an hour of scanning I had a list of nearly 200k subdomains which I was able to enumerate in greater detail with tools such as subjack and massdns.
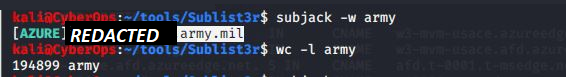
Soon after I discovered multiple domains that had CNAMES resolving to Azure domains that responded with NXDOMAIN. (An NXDOMAIN error message means that the domain does not exist.)
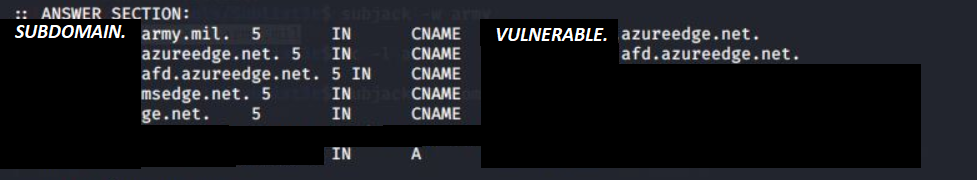
There are a few types of subdomain takeovers. In this article the CNAME method was used, I will briefly explain the other methods.
1. Name Server (NS) subdomain takeover
Same method from CNAME can be carried to NS subdomain takeover,
If the base domain of the CNAME of a NS record is available to register, the source domain name is potentially vulnerable to subdomain takeover.
2. MX subdomain takeover
Unlike the CNAME and NS subdomain takeovers, Mail Exchange (MS) subdomain takeover poses the least security severity and that is because mail exchange records are only used to receive e-mails. Gaining access over one would allow an attacker to receive e-mails designated to the domain source. This is commonly used in spear phishing attacks.
Exploiting / PoC
So far there is a potentially vulnerable CNAME that is registered with Microsoft Azure, so I quickly registered a free tier account. Luckily for me Microsoft credited my account with £150 worth of credit to spend for the month. However I didn't need any credits in order to perform the takeover.
Once registered I was able to browse the Azure services to create a CDN endpoint, Configure the new CDN profile to route to a location of my choice, within the cdn profile I had to set a custom domain, this will be the 'vulnerable' subdomain. Note: Cdn might need purging due to caching, everytime I made a new change to the web server content.
These are a few common vulnerable services under Microsoft Azure:
*.trafficmanager.net
*.azurewebsites.net
*.azureapp.com
*.azureedge.net
Next stage was to check and see if the I could register the CNAME in question and to my surprise it was free to register. Once that was done I was able to deploy a PoC to the server and check if I was in control.
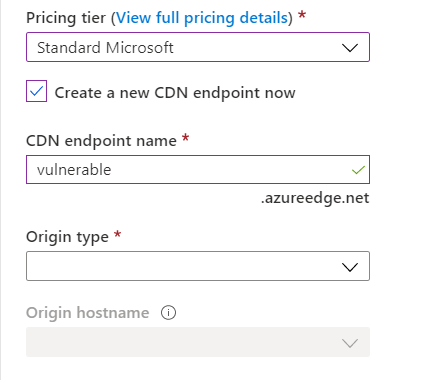
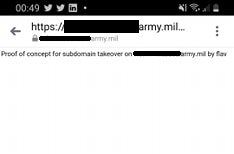
Reporting
Next step is pretty straight forward, I went back on HackerOne and clicked to submit a report for the U.S. Dept Of Defense.
I wrote to them in easy steps how I performed all this and where to check for my PoC, they quickly confirmed and fixed the issue.
This Vulnerability Disclosure Program (VDP) is active on H1 by the D.o.D, it is not eligible for bug bounty however for me it's a learning curve and I'm glad I assisted them in solving this critical vulnerability. In exchange I received a 'thank you' on HackerOne!
If you would like to see the report:

Thank you for reading my article, Until next time!
Read more about Other Vulnerable Cloud Providers
Your friendly neighbourhood Hacker.
