Synack Red Team Member
I've glad to share that I am finally a member of Synack Red Team. My actual offical joining date is 26/8/2021. It was a long process but very satisfying in the end. Tune in if you would like to know more about the journey!
Theodore Roosevelt: Nothing worth having comes easy.
This article is not sponsored by Synack or HackTheBox.
Introduction
Bug bounty programs were created 10-15 years ago by companies like Google, Mozilla, Facebook, they were basically created to help them uncover the security vulnerabilities that would ultimately lead to a major data breach. They opened up their environments to the world and said: "If you are able to find a vulnerability in one of our environments we will pay you, and we will pay you based on the impact and severity of that vulnerability."
About Synack
As Jay Kaplan Cofounder & CEO Synack said "Synack is the company that the world's largest corporations and government agencies turn to read their applications and networks of critical vulnerabilities, their customers range from the largest global 2000 companies, the world's leading banks, retailers, and health care organisations, they represent over a trillion dollars in assets, as well major federal agencies including the dept. of defence, dept. of energy, health and human services, they work with 18 different federal agencies today. They leverage a network of over 1500 of the most elite ethical hackers from 82 countries who are on the hunt for potential fatal vulnerabilities while utilising technology to make those hackers smarter and infinitely more skillable.
The word hacker [ hak-er ] traditionally has carried a pretty negative connotation and generally think of a hacker as a person wearing a hoodie, sitting in their parents dark basement and hacking by night and sleeping during the day. The reality is most of these really good hackers are true professional, they have normal 9 to 5 jobs working at some of the biggest companies in the world. The way we perceive them vs the way the look in reality is sometimes different.
There are several hackers that have passed a million dollar mark with Synack in terms of total money taking home over the past several years, so the ability to earn a substantial amount of money is real. Some hackers may earn several hundred dollars for finding low hanging fruit vulnerabilities or even completing "a mission"; is what they call at Synack, which is a task set up by Synack for researchers then they pick the mission, once completed they will be paid for it.
An example of a mission: It could be looking for Cross site scripting within the scope that they provide.
They will pay based on the category of the issue that the researcher finds, and the data that is ultimately exposed, all of that is fed into a calculation to determinate how much to pay the security researcher. Some people have shifted from their normal daily jobs to work full time on Synack.
Synack is kind of the Uber for Cyber Security with a lot more security controls in place, they aren't about big numbers of researchers, they are about the best of the best that's why they have a 10% acceptance rate of who they take into their community. They are really focus on people who are productive, they actively manage their community and make sure that those who are working with them are productively finding vulnerabilities and providing vulnerabilities to their customers."
SRT Member's Statements
Jennifer Villareal Ethical Hacker at Synack said "If you are a person who would rather not sit around and watch movies, if you'd rather be participating in something puzzle-like, and learning something that can make you money. People's privacy and national security may also be good motivation."
Jonnathan Villareal Ethical Hacker at Synack said "It's the coolest thing to ever to hack and get paid for it, and of course not going to jail is a huge plus too.
The satisfaction of knowing that you contributed to make something secure, if you can't break it and some of the best hackers can't break it today, means that people relying on these services can use them reliability and securely and there is a bit of pride to that as well."
Cyber criminals are hiding hard during the Covid19 pandemic and the crowdsource security testing model is essential for helping these organisation defend themselves especially when traditional security teams can't even get into the office.
Cyber Security is one of these industries where companies have been very sensitive and been against the idea of remote work but obviously that is changing in big way today.
Right now companies are trying to push new environments, new applications, new websites as fast as they can so they need a solution that allows them to thoroughly test these environments in a highly rapid manner.
How Synack gets the world best ethical hackers

Earning a spot on the Synack Red Team (SRT) is a pinnacle achievement in the career of the world's best security researchers, Synack has the most strict entrance criteria in the industry. Synack keep average hackers Out, even many above hackers won't make it to the SRT, uniquely Synack regularly removes SRT members each year, companies aren't exposed to ineffective testers protecting them in ways bug bounty platforms don't. This way their customers get the best of the best. The SRT members are incentivised to find unknown, high severity vulnerabilities in their customer's systems before these vulns will cause problems for the business. The SRT use Synack's platform to narrow in on critical vulnerabilities other solutions struggled to find, with Synack's proprietary scanning technology they can be more efficient than unassisted hackers seeking bug bounties on other platforms. Synack testing is also safer for companies with constant measurement, analytics and monitoring. Synack motivate the SRT members to do the best hacking including a Hall of Honour, The "Synack Acropolis", they continue to motivate the SRT as they climb the ranks. And finally to attract there are opportunities to travel, adventure and hack for Synack at destination events - all to protect their customers around the world.
About the Journey
Entry Point 1
There are two main ways to join the SRT, one of which is through their main website and through hackthebox tracks. The power behind the Synack platform is an elite team of the world's top cybersecurity researchers—drawn from over 80 countries, recruited for their skill, and chosen based on trust. (Apply). You will have to fill a form with as much information to show Synack your worth, this includes:

Bug bounty experience (public / private) must list any public profile links
Job descriptions with detailed responsibilities
Relevant industry certifications
Industry/conference speaking experience
Any attributed CVEs
Tip: Do you have a friend who is actively hunting on the platform? perhaps they could refer you? this may help with your application.
RED TEAM RESEARCHER REQUIREMENTS CROWDSOURCED
PENETRATION TESTING: RESEARCHER TRUST AND SKILL
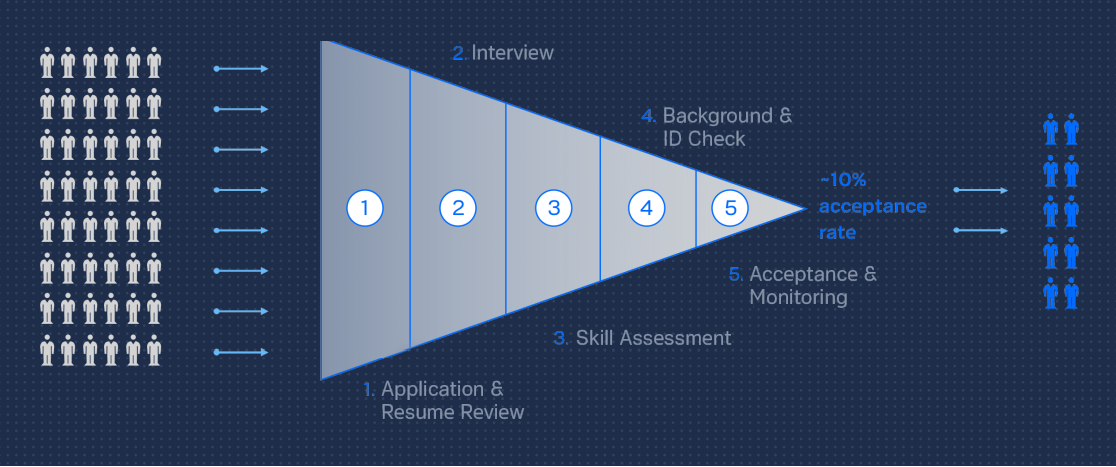
Synack Red Team (SRT) researchers must pass through a rigorous vetting process that includes five intensive vetting stages. SRT applicants must pass through all stages before being fully onboarded; this ensures that researchers are both technically qualified and trustworthy. Synack’s vetting process eliminates the majority of applicants with only ~10% fully passing through to the final on-boarding stage.
Synack Red Team Vetting Process
FRONT-END SCREENING: APPLICATION REVIEW
VETTING STAGES: APPLICATION, RESUME REVIEW AND INTERVIEW
Following an initial triage of applications, qualified candidates undergo a behavioural interview. Behavioural interviews are performed in-person or via video by trained and designated members of Synack’s Researcher Onboarding Team (ROT) to assess the candidate’s integrity and suitability for membership. During the interview, the ROT will establish a score for the candidate’s threshold for ethics, learn about candidate motivations and goals, and communicate Synack’s stringent requirements and expectations.
SKILL ASSESSMENT
VETTING STAGE: SKILLS TEST AND ASSESSMENT
Synack’s assurance that only qualified researchers will engage with client assets is enabled by our skill assessment program. Consisting of a written and practical application component, each skill assessment is specific to a technical domain, such as web or mobile application or host-based testing. To ensure fidelity, skill assessments are internally created, maintained and administered. Written and practical components may be taken only once, and must be completed in a single session.
TRUST ASSESSMENT
VETTING STAGES: BACKGROUND & ID CHECKS, ACCEPTANCE & MONITORING
Prior to onboarding, all researchers undergo a mandatory trust assessment consisting of background and identity verification and the following mandatory criminal background checks:
• Global terrorism and sanctions list search
• County criminal record history search (7-year)
• Department of Justice sex offender records search
• Federal Excluded Parties Listing System search A Social Security Number trace, including address history cross-referencing1 Once the researcher is admitted to the platform, they undergo a 45-day monitored qualifying period before being fully accepted into our program.
3.1 DoJ sex offender records search and Social Security Number trace are conducted for domestic candidates only.
What are the challenges?
You will typically be given up to 20 challenges that involve most common modern vulnerabilities being exploited in the wild. For confidentiality reasons I cannot go into this subject as much as I'd like to.

Once you complete your preferred route, you'll e-mail them and they will get back to you.
Aside proving your technical ability all the stages are just as important. You may have noticed Synack is very careful when picking their members.
Heads Up: You cannot collaborate with anyone on this, you cannot ask hints online. If you plan to cheat, then how will you be able to find vulnerabilities on the platform? After all, this is a job interview and if found in wrong you will definitely not proceed.
Entry Point 2
HACK THE BOX - (Method A and Method B).
Method A: Offshore

WHAT IS OFFSHORE?
Assess, Gain, Pivot. Real-World Active Directory Simulation!
Offshore Pro Lab is an Active Directory lab that simulates the look and feel of a real-world corporate network. You are an agent tasked with exposing money laundering operations in an offshore international bank. As a real-world penetration tester, you need to assess the external perimeter, gain an internal foothold and pivot across multiple hosts and forests.
Users start from an external perspective and have to penetrate the "DMZ" and then move laterally through the CORP.LOCAL, DEV, ADMIN and CLIENT forests to complete the lab. To track progress, there are multiple flags planted along the way as well as a few side challenges not required to advance within the Active Directory environment. Players can submit flags to earn a place in the Offshore Hall of Fame and receive badges for various stages of completion.

Who is Offshore for?
Offshore Pro Lab has been designed to appeal to a wide variety of users, everyone from junior-level penetration testers to seasoned cybersecurity professionals as well as InfoSec hobbyists and even blue teamers; there is something for everyone. Players will pick up multiple new tricks and hacks, which can be immediately applied to real-world engagements or taken back to their organizations to help improve the overall security posture.
SKILLS / KNOWLEDGE
- Familiarity with modern tools and techniques used to perform Penetration Testing engagements
- Working knowledge of Networking and Web Application Attacks
- Working knowledge of Linux and Windows Operating Systems and Active Directory
ATTITUDE / MENTALITY
- Patience and perseverance
- Willingness to do extensive research
- Accept that you might fail more times than you will succeed; it's part of the process
What will you gain?
Are ready to develop and enhance your skills in network penetration testing?
Players will gain the opportunity to attack 17 hosts of various operating system types and versions to obtain 30 flags across a realistic Active Directory lab environment with various standalone challenges hidden throughout. Some of the Red Team TTPs (Tools, Techniques, Procedures) players will learn include:
- Web Application Attacks
- Enumeration
- Exploiting Obscure and Real-World Active Directory Flaws
- Local Privilege Escalation
- Lateral Movement and Crossing Trust Boundaries
- Evading Endpoint Protections
- Reverse Engineering
- Out-Of-The-Box Thinking
Offshore Lab is not free, players that have completed Offshore will own a certificate of completion provided by Hack The Box.
All Hack The Box players that successfully complete (100%) Offshore Pro Lab [Penetration Tester Level II] get one step closer to joining the Synack Red Team. All you need to do is complete Offshore within this timeframe and send an email to [email protected] with the subject "Offshore Completed" including your official HTB certificate of completion.
Method B: Synack Red Team Track
A great way to fast-track your application to join SRT through Hack The Box, the Synack Red Team Track!
Have you discovered our newly announced Tracks? If not, let’s cut straight to the chase and explore Hack The Box Tracks on the new platform.

One of them is the Synack Track, including 7 HTB Machines and 7 HTB Challenges. Create beautiful exploit chains, master some of the most interesting web vulnerabilities, and prove your prowess in the specially curated Synack Red Team Track.
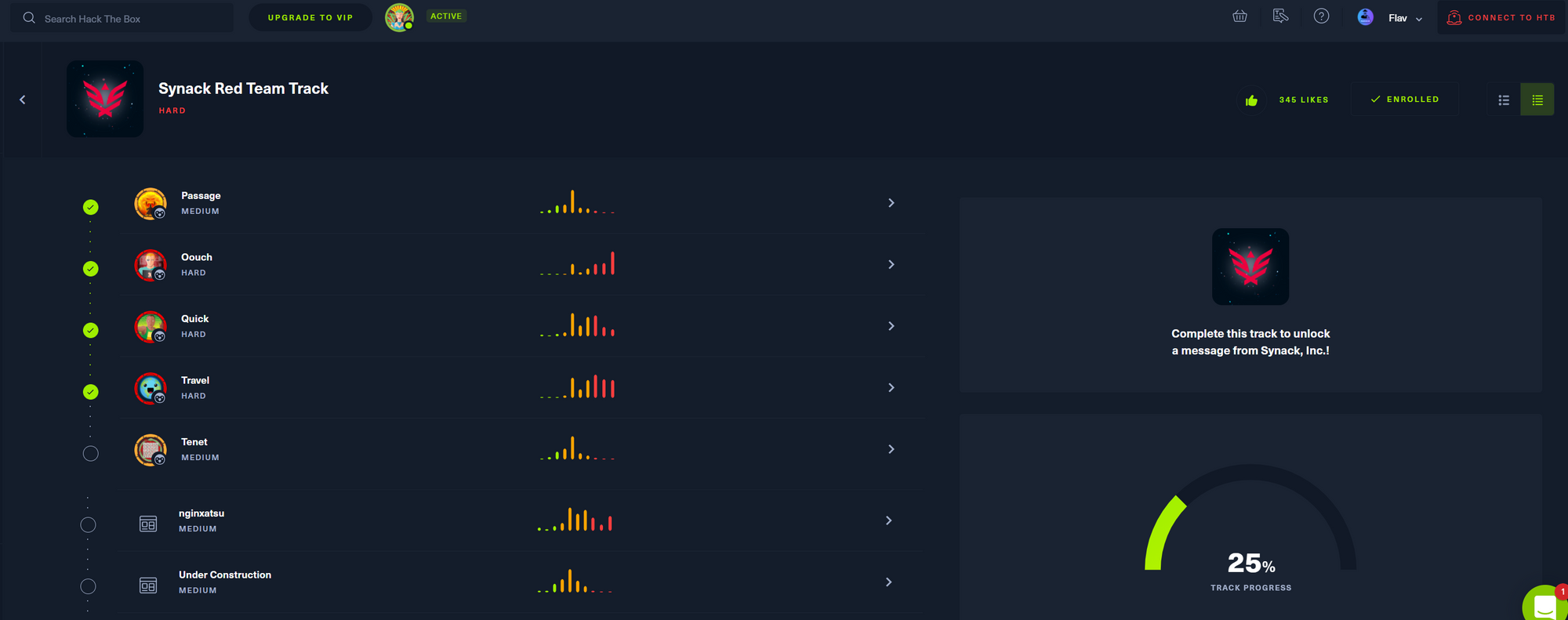
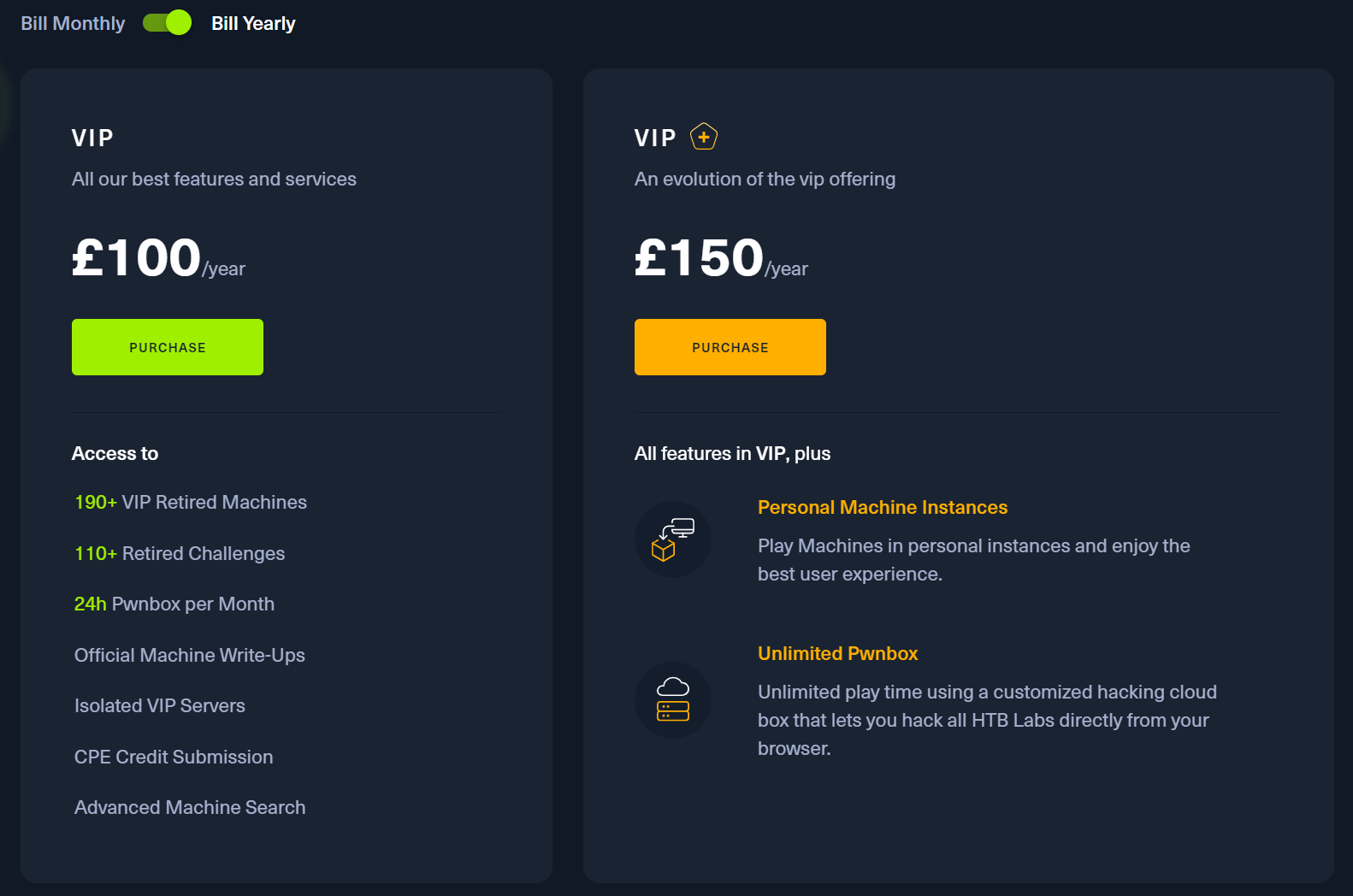
Due to some machines being retired that are part of the track, you will need a VIP subscription to be able to spawn these boxes.

As Ryan Rutan, Director of Community at Synack said "We are very excited about this joint effort with Hack The Box as it will help many up and coming security professionals test their talents as a potential member of the Synack Red Team.
As a valued Hack The Box user, you have had the opportunity to test and improve your cyber security skills using the HTB training platform. Given your track record, we feel you have demonstrated the skills needed on the Synack Red Team to provide crowdsourced security testing.
Synack responsibly grows the SRT proportional to the opportunities that are available to the community. This ensures both an equitable, yet competitive, landscape that strives above all else to be fair and respectful to each SRT such that they can hack, learn and grow as security professionals. Synack leverages an application waitlist to ensure that growth is always strategically aligned in this regard."
Conclusion
I have been super excited to explore the platform, complete a few missions, find a few bugs, learn along the way and level UP!
So far I am just beginning to get used of how things are getting done, but see a print of my current stats.
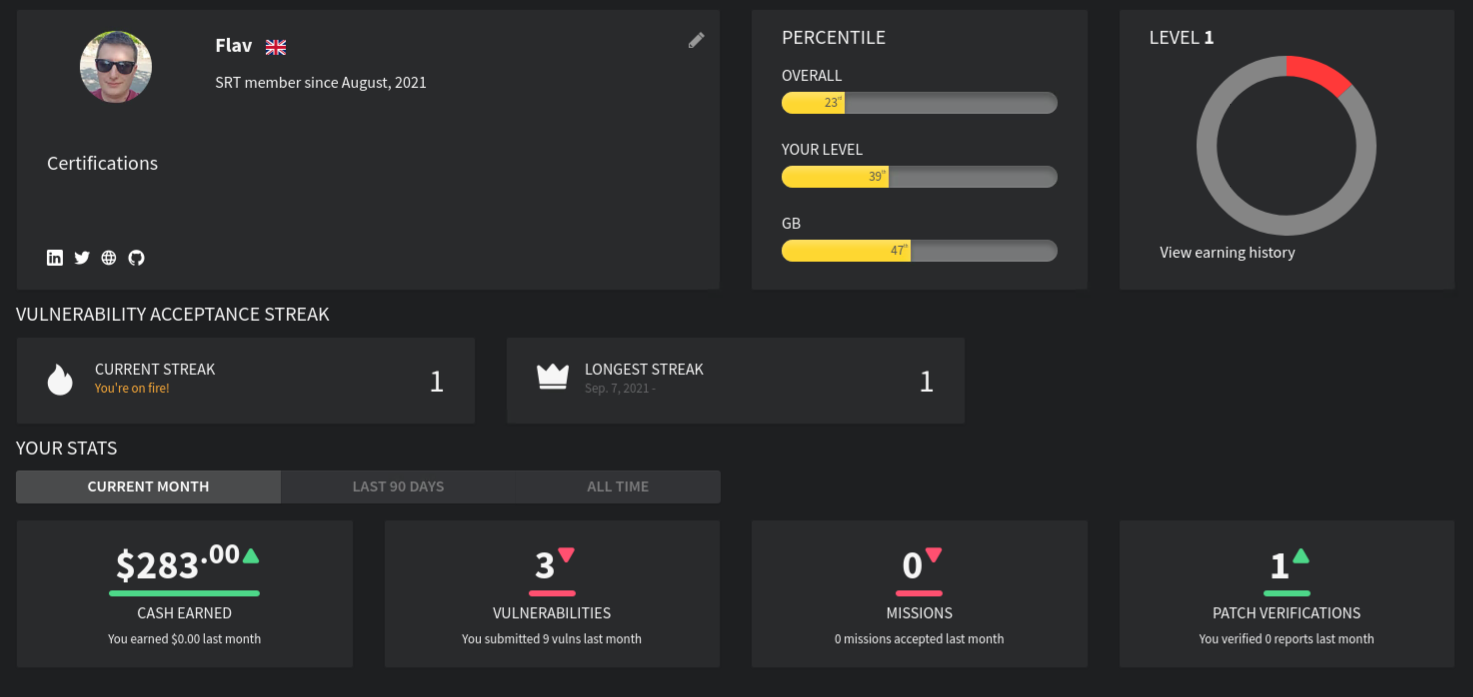
If you decide this is for you, I wish you all the best on your journey! don't get demotivated if somebody says you can't do it. Instead accept it as a challenge, give your best, work hard and prove your worth.
Sources:
Synack Requirements
HackTheBox Tracks
Have you got any suggestions or questions for me ? Get in touch!
Thank you for reading my article, Until next time!
Your friendly neighbourhood Hacker.
